Headlines around the world screamed about the data breach impacting 100 million Capital One customers in the U.S. and 6 million customers in Canada.
The suspect in this case, 33-year-old Paige A. Thompson, was an insider of the most dangerous kind: a former white hat hacker who apparently went to the dark side and started using her powers for evil instead of good.
Our team just finished reviewing the court documents in this case, and some of the details could be particularly interesting or helpful for the cybersecurity leaders and teams we serve at SecureWorld conferences across North America.
With that in mind, let's take a look at what is revealed in the court documents about the Capital One hacker.
8 cybersecurity details revealed in court about the hacker who breached Capital One
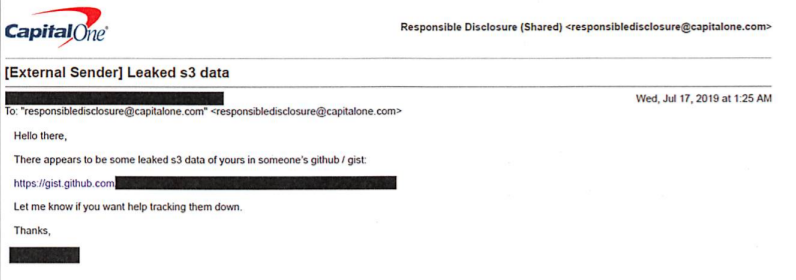
1. She was caught after posing as a white hat hacker trying to disclose a leak.
According to Department of Justice documents in the case, "On July 17, 2019, an individual who previously was unknown to Capital One" emailed the company's "responsible disclosure address" to alert them to leaked cloud data.
2. Even though she used a VPN and the TOR router to anonymize her activities, she got sloppy with GitHub.
"The individual's e-mail stated that there appeared to be leaked data belonging to Capital One on GitHub, and provided the address of the GitHub file containing this leaked data. The address provided for this file was...Paige A. Thompson's full first, middle and last name."
3. After receiving this tip, Capital One examined the GitHub file and discovered an April 21 timestamp and the IP address for a specific server, which revealed the cyberattack:
"A firewall misconfiguration permitted commands to reach and be executed by that server, which enabled access to folders or buckets of data in Capital One's storage space at the cloud computing company. [Note: this was AWS]
Capital One determined that the April 21 File contained code for three commands, as well as a list of more than 700 folders or buckets of data."
Those commands enabled the hacker to obtain security credentials for greater access, enabled her to produce a list with the names of folders or buckets of data Capital One had at AWS, and to extract data from those folders.
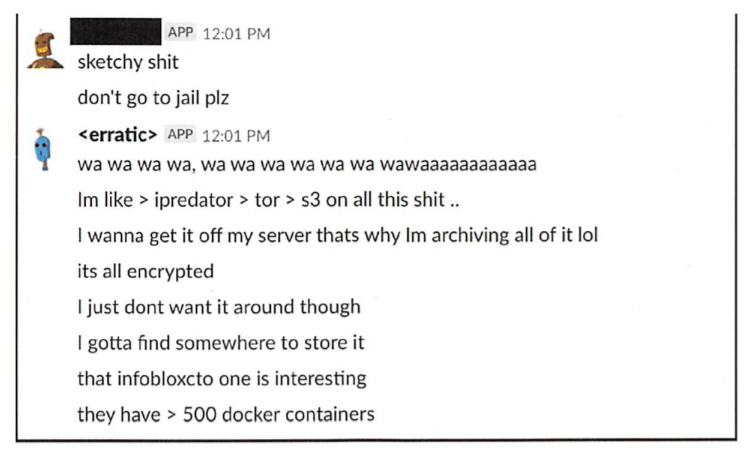
4. The Capital One hacker started bragging about her crimes in a Slack channel, on social media, and in a Meetup group.
"On or about June 27, 2019, another user posted 'don't go to jail, plz.' In response, erratic [her screen name] posted 'Im like >ipredator>tor>s3 on all this sh*t.'"
And she went on to write:
"I wanna get it off my server that's why I'm archiving all of it lol."
Here is that discussion from court documents:
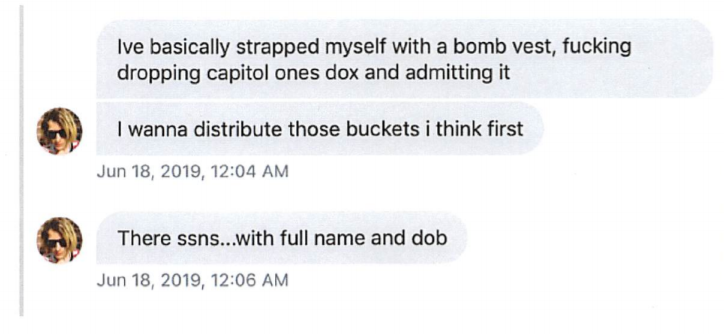
5. Capital One helped prosecutors with this investigation, and in a number of cases provided evidence from the company's internal research on the suspect.
"According to a screenshot that Capitol One provided, on June 18, 2019, Twitter user 'ERRATIC' [Paige Thompson's screen name] sent a direct message to the reporting source: 'Ive basically strapped myself with a bomb vest, fucking dropping capitol ones dox and admitting it. I wanna distribute those buckets i think, first.'"
She also bragged about having Social Security numbers in the stolen data:
6. The Capital One hacker used several technologies to try to avoid detection. Court documents reveal that she used:
• IPredator, which is a prepaid VPN service
• Meetup, which allows people to find and build online communities
• Slack, on which she used a specific "channel" with those she trusted
• GitHub, where she hosted the files she allegedly stole from Capital One's AWS account
• The Onion Router (TOR), which helped her stay anonymous as she was working on the AWS server and extracting the S3 bucket data
7. Paige Thompson used to work for Amazon Web Services (AWS) as a "Systems Engineer" during 2015-2016.
Court documents also revealed an extensive online resume, which shows the Capital One hacker started her IT career as a sysadmin for a software company and then a school, followed by roles as a software engineer and systems architect. View her online resume here.
And CBS News interviewed a former employer:
Neo Nasrati, CEO of ColumbusSoft, which acquired Seattle Software Solutions from its previous owner, said Thompson was a "very talented 'white hat' ethical hacker" who excelled at testing clients' security systems for flaws. "She was involved in the hacker community, but from what I knew of her I don't see how she would have done anything illegal."
8. The Capital One hacker may have breached other companies as well, according to court documents in the case:
"On or about June 27, 2019, 'erratic' posted about several companies, government entities, and educational institutions. During the initial search of some of these devices, agents observed files and items that referenced Capitol One and the Cloud Computing Company, other entities that may have been the targets of attempted or actual networking intrusions, and 'erratic,' the alias associated with Paige A. Thompson."
Sometimes when a suspect is arrested, it's the end of revelations about their crimes; in other cases, it is just the start.
We'll let you know what happens in this case.
Capital One reveals data encryption and tokenization details
And there is one more very interesting cybersecurity fact that's been revealed, this time by Capital One itself, about the data it encrypts and tokenizes:
"We encrypt our data as a standard. In addition, it is our practice to tokenize select sensitive data fields, most notably Social Insurance Numbers and credit card account numbers. Tokenization involves the substitution of the sensitive field with a cryptographically generated replacement. The method and keys to unlock the tokenized fields are different from those used to encrypt the data.
Due to the particular circumstances of this incident, the unauthorized access also enabled the decrypting of the data."
The realities of that last line probably felt like a sucker punch to Capital One's incident response team.
[RESOURCE: Watch the SecureWorld web conference, Cloudy with a Chance of Breach. The expert panel discussion on cloud security is available on-demand.]
[RELATED: Capital One Data Breach Information Page]