North Korea has been busy using a new tunneling tool against North American cyber targets.
Now CISA and US-CERT are alerting on ELECTRICFISH with a new malware analysis report.
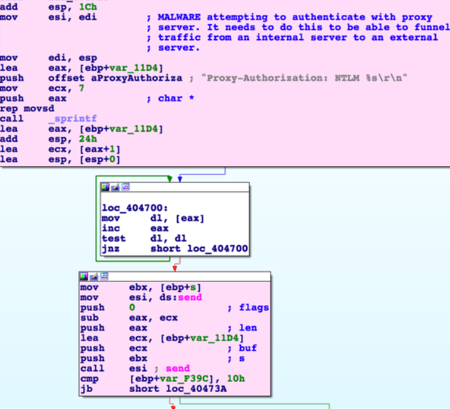
The report provides analysis of one malicious 32-bit Windows executable file.
"The malware implements a custom protocol that allows traffic to be funneled between a source and a destination Internet Protocol (IP) address. The malware continuously attempts to reach out to the source and the designation system, which allows either side to initiate a funneling session.
The malware can be configured with a proxy server/port and proxy username and password. This feature allows connectivity to a system sitting inside of a proxy server, which allows the actor to bypass the compromised system’s required authentication to reach outside of the network."
How to mitigate risk from North Korea malware
CISA (Cybersecurity and Infrastructure Security Agency) issued a list of about a dozen steps your organization can take to minimize the risk of falling victim to the ELECTRICFISH malware.
Most of them belong on a cybersecurity fundamentals list. Keeping up on patching, for example, is one of the best practices. Here are some additional mitigation efforts:
- Disable File and Printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
- Restrict users' ability (permissions) to install and run unwanted software applications. Do not add users to the local administrators group unless required.
- Enable a personal firewall on agency workstations, configured to deny unsolicited connection requests.
- Scan for and remove suspicious email attachments; ensure the scanned attachment is its "true file type."
You can read the complete Homeland Security CISA advisory on North Korea and ELECTRICFISH for yourself.
Also, remember our free SecureWorld resources, on varying topics, are available online. This includes these upcoming cybersecurity web conferences:
Email Fraud Case Studies: Real-World Attacks and Defense Strategies
Time Is Up: Re-Think DLP