A few weeks ago, the popular and controversial hacktivist group known as Anonymous declared war on Russia following President Vladimir Putin's decision to invade Ukraine.
The group called on local hackers and members of the cybersecurity community in Ukraine to fight back against Russia, asking them to submit applications via Google docs, listing their specialties (such as malware development) and professional references.
Those volunteers were divided up into offensive and defensive units. The offensive unit would help Ukraine's military conduct digital espionage operations against invading Russian forces, while the defensive unit would be employed to defend critical infrastructure such as power plants and water systems.
Since then, the group has made some pretty significant progress on the cyber front, according to Jeremiah Fowler, a co-founder of cybersecurity company Security Discovery.
Hacktivists target Russian media and government sites
Fowler recently published a report detailing what has unfolded since Anonymous declared cyberwar against Russia. He is currently located in Poland, where he has been monitoring cyber activity from both sides. When everything started unfolding with Russia, he was quick to jump in and help. Fowler writes:
"For the record, I am an American citizen who has lived and worked in Ukraine for nearly a decade. In the early morning hours of February 24th the Russian invasion of Ukraine began. I packed up a few belongings, computers, hard drives, and personal items and fled the city of Kyiv as fast as possible. By 7 a.m. there were already hours long lines to gas stations and major roadways were nearly stopped with traffic. It took four agonizing days to get to the Polish border where over 115,000+ Ukrainians had crossed in just the first three days alone."
As an ethical security researcher, he says he always looks for exposed data and information but would never target any specific organization or geographic location. In this report, he looks at publicly exposed data that was hosted on IPs located in the Russian Federation that also use non-password protected cloud storage repositories.
Fowler continues on to discuss specific success he has seen against Russia:
"Since the start of the conflict members of Anonymous and other groups have targeted Russian state media outlets, government websites, and what appears to be any Russian and Belarussian database that was already exposed or newly misconfigured datasets.
This is an example of how a single cause can unite a global network of individuals outside of any government control.
Reports claim that Anonymous has disrupted websites of the oil giant Gazprom, the state sponsored news channel RT (Russia Today) and shut down the Control Center of the Russian Space Agency 'Roscosmos.' On March 7th 2022, Anonymous claimed to hack Russian state TV stations Russia 24, Channel One, and Moscow 24 to air footage of the war in Ukraine which many Russian citizens are unaware of.
In addition to hacking, there have been significant denial-of-service (DDoS) attacks where the website's server is overwhelmed with traffic and unable to function. These attacks are often distributed among so many machines, devices, and IP addresses that they are nearly impossible to defend against."
Fowler also notes that in a random sampling of 100 Russian databases, 92 had been compromised, with one of them belonging The Commonwealth of Independent States (CIS). The CIS was established after the fall of the Soviet Union in order to help facilitate trade, finance, lawmaking, and security between CIS member states.
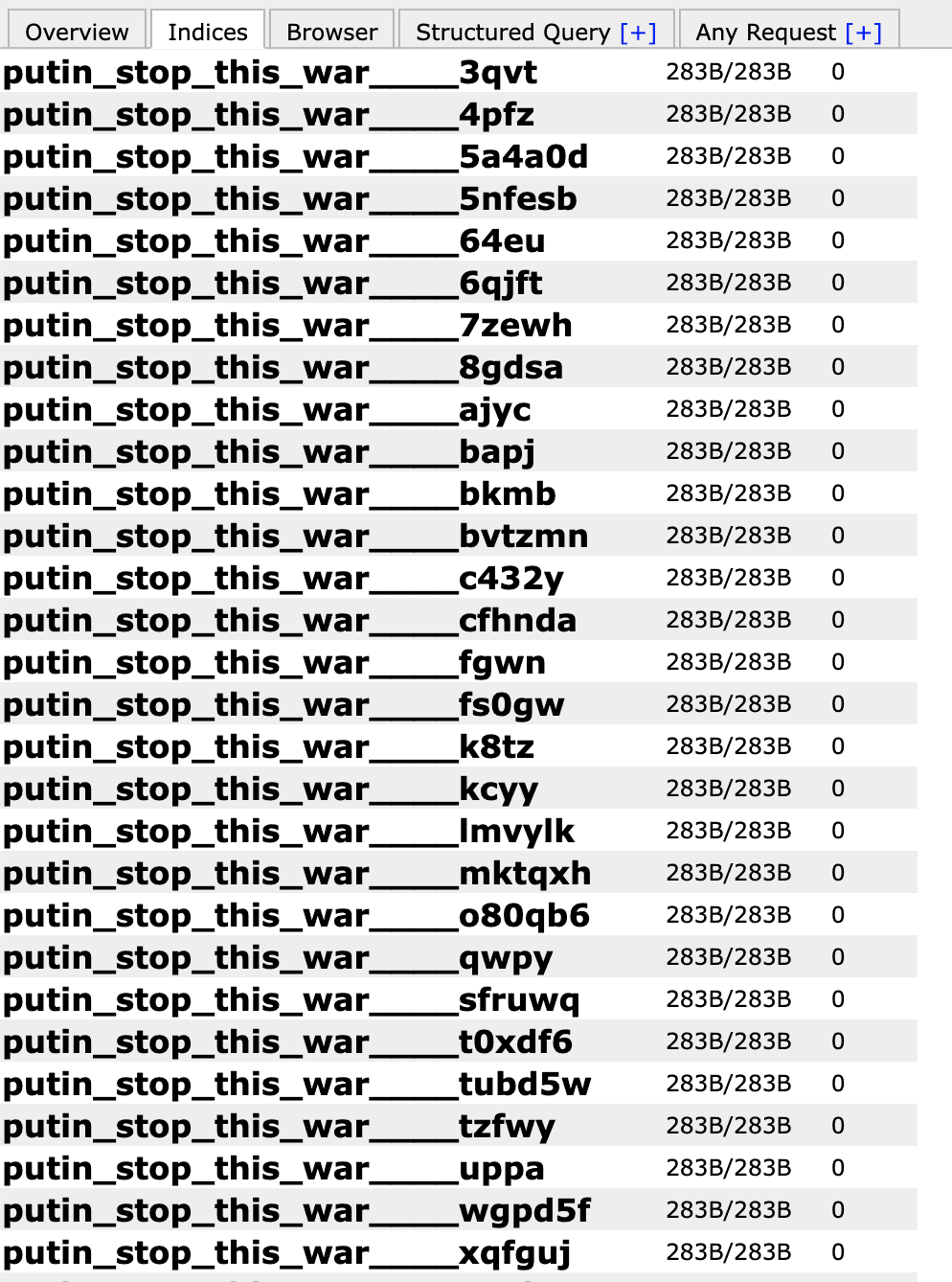
Below is a screenshot of one of the Russian databases, with files deleted and folders named "Putin Stop This War." The "0" listed in the last column is the number of files in the folder.
Anonymous is a highly capable group when it comes to hacking and disruption, so it will be interesting to see what unfolds next. Check out Jeremiah Fowler's report, Hacker Group Anonymous and Others Targeting Russian Data for more information.




