Imagine what this day would be like.
You've worked hard. Your investments have paid off.
You sign on the dotted line to buy that million dollar yacht you've always dreamed about.
You had told your financial advisor all about it so he wouldn't be surprised you'd be tapping into your investments.
Then your email comes, asking him to make a wire transfer of more than $200,000 of your money as a partial payment.
He follows your request—and suddenly your dream becomes a nightmare.
The adviser unknowingly sent your $200k to hackers.
The email requesting the transfer was not from you, but it sure looked like it was. And the timing of the fake request was nearly perfect.
"These are not hackers sitting in your grandma’s basement and eating Cheetos," says Stephen Dougherty of the United States Secret Service. "These are sophisticated operations where they decide who they want to target as victims."
Dougherty is a financial investigator contractor who works in the Secret Service's Global Investigative Operations Center (GIOC).
He investigated this specific yacht sale/financial advisor BEC scenario. And he shared several additional BEC case studies in the SecureWorld web conference, Email Fraud Case Studies and Defense Strategies, which is available on demand.
He also talked about the risk to organizations and the U.S. economy because of business email compromise.
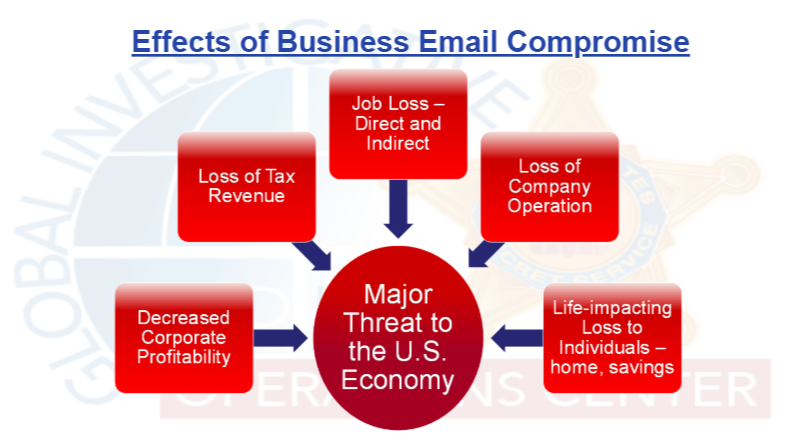
How do BEC scammers operate?
Dougherty says it starts with searching for potential targets. After all, experienced hackers have a good idea which type of targets are most lucrative.
Next, a handcrafted email or series of spear phishing emails are sent to targets at that company.
[RELATED: Spear phishing was one of the 20 steps used to hack the DNC]
If all goes right for hackers, those receiving the phishing email will type in their login credentials to the hacker created form. At that point, the hackers get access to the employee's account. And they know exactly what to do next, according to Dougherty.
"Once the criminal actors gain access to email accounts, the most common form of surveillance is to set up email rules in the account settings to auto-forward emails then delete them to avoid detection. Other than the email rule, no evidence of the surveillance is visible."
Cybercriminals then read those auto-forwarded emails, picking up details on wire transfer amounts, payment due dates, and more. That is how hackers in the financial advisor/yacht case knew to send a request for yacht payment for the right amount, at the right time.
They were in the financial advisor's email, watching the conversation unfold one electronic line at a time.
Cyber defense against BEC and social engineering attacks
If those who perpetrate Business Email Compromise continue to profit from it, then what are the cyber defense strategies that actually help your organization defend against it?
Ryan Terry, Manager of Product Marketing at Proofpoint Security, presented several best practices in the web conference that can help with BEC defense.
He explained how the proven control for domain spoofing is DMARC email authentication; that the proven control for look-alike domains is domain monitoring; and that the proven security control for display name spoofing is based on Machine Learning and related policy.
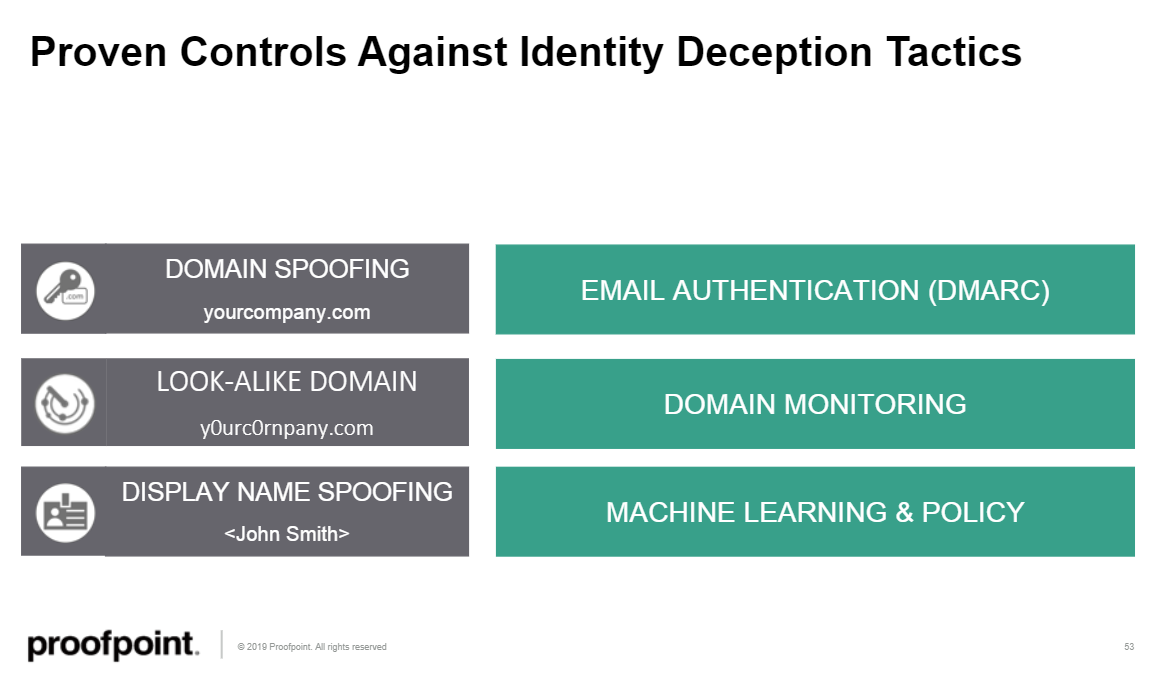 He also explained how other security controls fail against BEC attacks:
He also explained how other security controls fail against BEC attacks:
“The attackers are just sending, really, a few well-crafted emails to targeted people at the right time. A lot of these don’t have any malicious payload, they simply have text that instructs the end user on what to do. Because there is no payload, antivirus and other defenses cannot really stop them.”
The number of BEC attacks is skyrocketing
Terry also says Proofpoint is tracking a surge in BEC attacks and credential compromise via phishing:

And he addressed the question of who is at risk. According to Proofpoint research, the risk of BEC compromise cuts across industry verticals, organizational size, and individual roles.
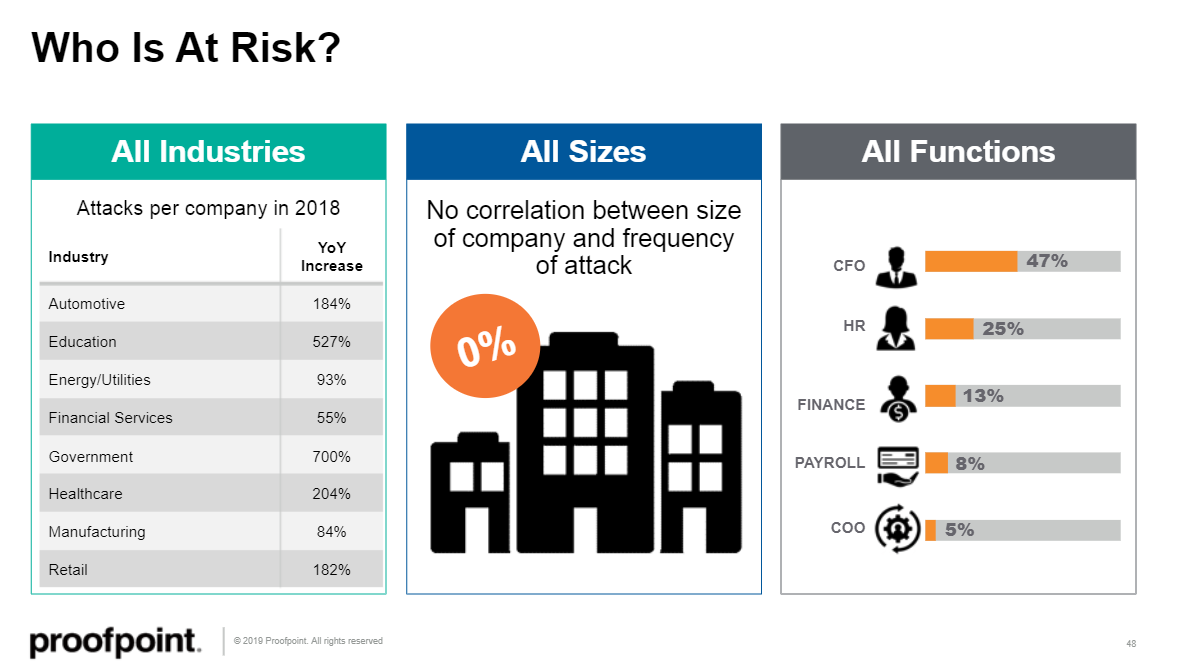
Listen to the web conference for much more on BEC
These are just a few of the highlights from our recent SecureWorld web conference, Email Fraud Case Studies: Real-World Attacks and Defense Strategies, which is available on-demand.
The speakers also unpacked who to contact, and when, if you realize your organization has fallen for a BEC scam, along with more on how the financial incentives for committing this type of cybercrime are extremely strong.
We encourage you to share this information with your peers and leaders at your organization. And so does Stephen Dougherty of the United States Secret Service, who puts it like this:
"The best defense against BEC is an informed and vigilant population."




