The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has released a joint Cybersecurity Advisory (CSA), with the National Security Agency (NSA) and the Federal Bureau of Investigation (FBI), detailing the top Common Vulnerabilities and Exposures (CVEs) exploited by Chinese state-sponsored threat actors since 2020.
CISA says that Chinese threat actors continue to exploit known vulnerabilities to target networks of the United States and its allies, as well as tech companies, to steal intellectual property.
The CSA aims to inform all federal and state government agencies, specifically those involved in critical infrastructure, and private sector organizations of notable trends and commonly used tactics, techniques, and procedures (TTPs).
Here are some technical details included in the advisory:
"NSA, CISA, and FBI continue to assess PRC state-sponsored cyber activities as being one of the largest and most dynamic threats to U.S. government and civilian networks. PRC state-sponsored cyber actors continue to target government and critical infrastructure networks with an increasing array of new and adaptive techniques—some of which pose a significant risk to Information Technology Sector organizations (including telecommunications providers), Defense Industrial Base (DIB) Sector organizations, and other critical infrastructure organizations.
PRC state-sponsored cyber actors continue to exploit known vulnerabilities and use publicly available tools to target networks of interest. NSA, CISA, and FBI assess PRC state-sponsored cyber actors have actively targeted U.S. and allied networks as well as software and hardware companies to steal intellectual property and develop access into sensitive networks. See Table 1 for the top used CVEs."
The top 20 vulnerabilities exploited by Chinese state-sponsored threat actors since 2020 are:
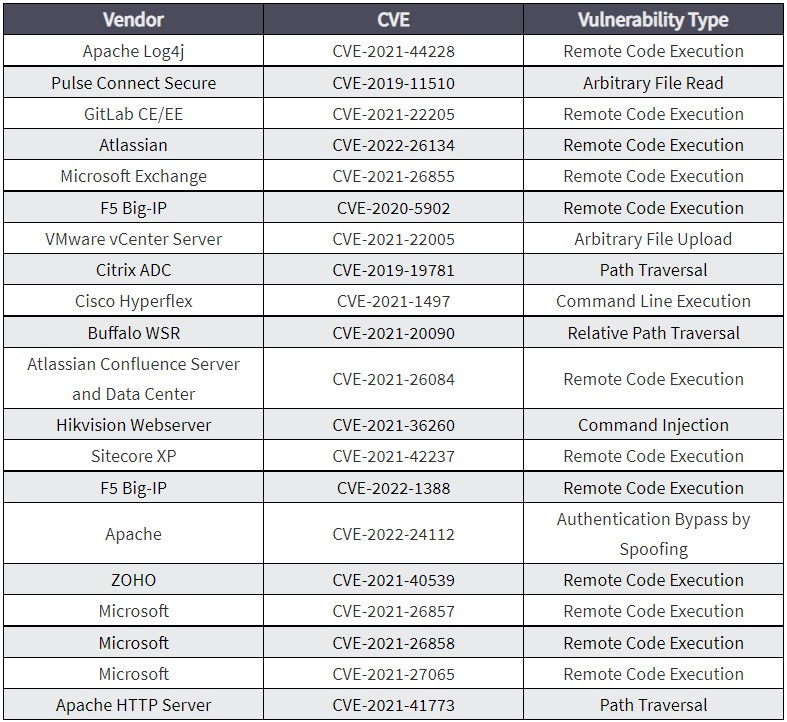
The threat actors exploiting these vulnerabilities often use VPNs to hide their activities and target web-facing applications to gain initial access. A majority of the vulnerabilities listed above allow hackers to quietly gain access to networks, where they establish persistence and move laterally in other connected networks.
So, what can you do to better protect your organization from Chinese hackers? The advisory provides six mitigations:
- "Update and patch systems as soon as possible. Prioritize patching vulnerabilities identified in this CSA and other known exploited vulnerabilities."
- "Utilize phishing-resistant multi-factor authentication whenever possible. Require all accounts with password logins to have strong, unique passwords, and change passwords immediately if there are indications that a password may have been compromised."
- "Block obsolete or unused protocols at the network edge."
- "Upgrade or replace end-of-life devices."
- "Move toward the Zero Trust security model."
- "Enable robust logging of Internet-facing systems and monitor the logs for anomalous activity."
CISA, the NSA, and the FBI strongly encourage all organizations to review and apply these mitigations to improve their cybersecurity posture and minimize the risk of compromise.
For more information, see the complete advisory, Top CVEs Actively Exploited By People’s Republic of China State-Sponsored Cyber Actors.
Follow SecureWorld News for more stories related to cybersecurity.





