Cyber events continue to unfold in Russia and Ukraine as the conflict between the two countries continues to intensify.
The Conti ransomware gang—one of the most notorious cybercrime operations in the world, and notably tied to Russia—had 13 months of incredibly sensitive data leaked by a Ukrainian cybersecurity researcher, according to InfoRiskToday.
The anonymous researcher had access to Conti's internal systems and released the data following the ransomware gang's decision to support Russia in its invasion of Ukraine.
The data includes Bitcoin addresses, Jabber chat logs, and negotiations between Conti and its ransomware victims. A majority of the data contains internal discussions between members of Conti, including personal details, conflicts, and accusations.
Alex Holden, a Ukrainian-born citizen and founder of Hold Security, says the leaked data is "a must-read for any security professional because it gives you an insight of how ransomware really works." He also mentions the researcher:
"This is a Ukrainian citizen, a legitimate cybersecurity researcher, who is doing this as part of his war against cybercriminals who support the Russian invasion," Holden said.
Researchers from VX-Underground shared an image that accompanied the leaked data:
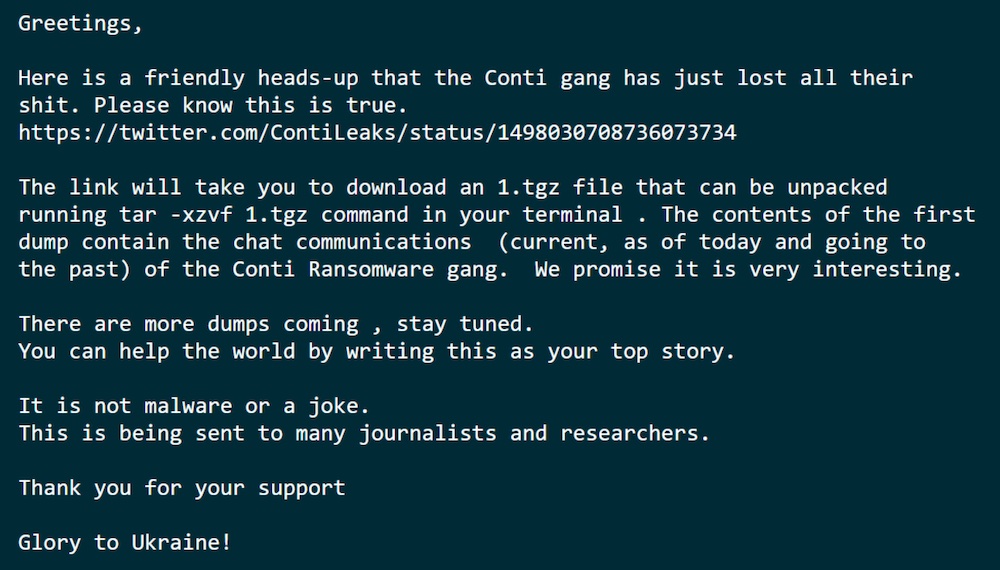
Bill Demirkapi, a security researcher who published a version of the logs translated into English, confirmed to The Verge that the logs contained details of Conti's technical infrastructure, logistical operations, discussions of Zero-Day vulnerabilities, and details about internal tooling.
Demirkapi says it will be difficult to assess the long-term impact the leak will have on the group given the short timeline since the release of the data.
Ransomware groups shy away from politics
It is well known that many of the notorious ransomware groups have been tied to Russia, but in practice, they are usually transnational entities with a diversity of nationalities, says Chester Wisniewski, principal research scientist at Sophos. He continues:
"The polarizing nature of this conflict—which effectively seems to be the whole world versus Russia—means there's way less [cybercriminal] activity than we expected. I think there's a lot of sympathy for Ukraine among members of these different groups, and as a result they're sitting it out."
Lockbit, a competitor of Conti, said it would not target Western allies because of the ongoing conflict in Ukraine:
"Our community consists of many nationalities of the world, most of our pentesters are from the CIS including Russians and Ukrainians, but we also have Americans, Englishmen, Chinese, French, Arabs, Jews, and many others in our team.
Our programmers developers [sic] live permanently around the world in China, the United States, Canada, Russia and Switzerland. Our servers are located in the Netherlands and the Seychelles, we are all simple and peaceful people, we are all Earthlings.
For us it is just business and we are all apolitical. We are only interested in money for our harmless and useful work."
While some ransomware groups have been able to disappear and return months later, it looks like that might be a bit difficult for Conti, considering the data contained in the leak. Brett Callow, a threat analyst from Emsisoft, thinks this could be the end for them:
"I'll be surprised if Conti recovers from this. The leak is devastating for them and, potentially, for anybody connected to them. Affiliates will be wondering how long the operation was compromised for and whether any information was obtained that points to them," Callow said.
Follow SecureWorld News for updates on the situation in Ukraine and Russia.





