It's not every day one gets to talk with the former CIO of the Executive Office of the President at The White House (and first female to hold the position), 2019 Women Cybersecurity Leader of the Year, and current CEO, Senior Partner and President of Fortalice Solutions, LLC.
But SecureWorld did just that on October 13th when we spoke with Theresa Payton on the topic of "Ransomware: Malware as an Ongoing Email Issue." The Remote Sessions webcast, available to watch on-demand, is the final installment of a three-part series on modern email attacks sponsored by Abnormal Security. Payton was joined by Abnormal Security CISO Mike Britton.
Why is ransomware a popular attack method? Payton said it's still prominent simply "because it works for ransomware syndicates. It is highly scalable and has a high ROI."
She said the first documented attack was in 1989 via a floppy disk, with the cyber attacker asking for a $189 ransom to be sent to a P.O. Box in Panama. Wouldn't victims love to only have to pay that much today?, she asked.
And there's no slowing down. By 2031, damages from ransomware attacks will cost $265 billion in U.S. dollars; by 2035, there will be about one attack every two seconds.
Britton said ransomware is "noisy" and a lot of attention and focus is put on it by media. Enterprises want to stay out of the news, and CISOs want to be able to answer their board when they ask if their company is at risk. His team talked to 300 security leaders about email-borne threats, and they ranked the following as the top ones: malicious attachments, ransomware via email, and credential phishing.
Unfortunately, email is an easy target, Britton said. It's the dominant mode of communication for every person and every business. A real insider threat is employees, disgruntled or not, who accept offers of payment to purposely be complicit in a scam of their company. Times are tough, people are struggling, so employees are vulnerable assets.
And much of it is innocent mistakes and gullibility. A bad actor may use a subscription renewal as the trick, the person maybe avoids the link but calls the number, then they are led to a URL that is a link to a ransomware attack. They are unknowingly duped, Britton said.
Fake calendar invites are another attack method, with virus-filled attachments, coding in the ICS "Add to My Calendar" link, and then employees are again downloading malware or ransomware unknowingly.
Emails look benign, Britton said, and email security solutions don't pick up on it as the messaging is not indicative of an attack. "Social engagement works; it's very sneaky," he said.
"Phishing is definitely the number one favorite delivery vehicle of ransomware," Payton said.
She also pointed out that not everything is as it appears to be; not all attackers are sophisticated nation-states that are well tuned. They are not any smarter than your teams, they just have time on their hands (which is a luxury most of us don't have), she said.
So should companies pay the ransom?
The conversation around being hit with ransomware should be "are we going to pay or are we not going to pay?" Payton said. Ideally, that conversation should happen before an incident ever happens.
"My goal would be that everyone who walks way from our time together would say 'I know everything we need to do so that we never have to pay.' That's my goal," she said.
Having that strategy really does work. As an example, Payton said a local government had a playbook and said they will never, ever pay a ransom. The insurance company got involved and said they will negotiate. The head of the government agency asked me what they should do, she said. "I told him that your playbook said you will not pay," she said. It was best to be transparent to constituents, not pay, and ask for patience as systems came back online. It's important to follow the playbook even under extenuating, stressful circumstances, Payton added.
"To me, one of the biggest pieces of advice is making sure you're focusing on a culture where people are comfortable raising their hands when they see something or make a mistake," Britton said. "Security is very much a team sport, so I rely on everybody throughout the organization to be the eyes and ears and let me know when something happened that shouldn't happen. It's all about how quickly we can respond and fire up the incident response playbook."
A ransomware response playbook cycle
Payton said a response playbook should be a dynamic, living, breathing document. It is a playbook for the team, the entire enterprise. They all need to understand their roles.
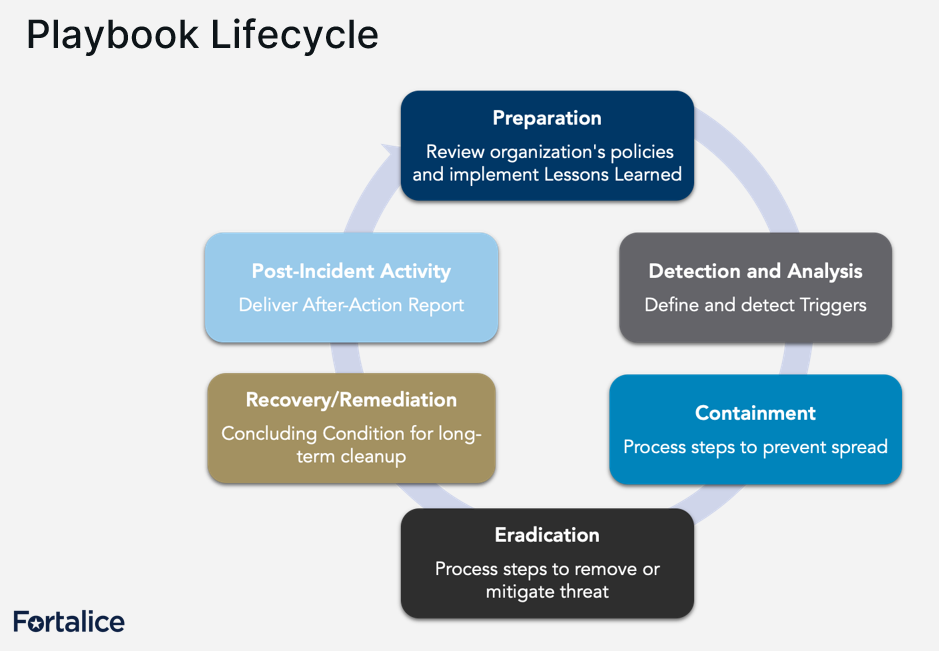
"A step often overlooked in lifecycle plans is post-incident activity," Payton said. "You must have an after-action report. You will not learn from your mistakes if you don't make everybody take a deep breath—and that's everyone, that's legal, compliance, insurance, procurement, third-party vendors—if you don't make everybody take time out to ask 'what worked well, what didn't work well, what could we do better?'"
Some key questions every cybersecurity leader should ask:
- What external teams have to be involved with the playbook process?
- Where is the contact information stored for these teams?
- Are these teams aware of these expectations?
- What security best practices could be integrated into the information technology standards?
BEC attacks continue to increase
The number one cybercrime is Business Email Compromise (BEC), Payton said. The FBI reports losses from BEC (globally) have gone up by 65%. It has hit all 50 U.S. states and 170 countries in the last 18 months.
The top list of countries that BEC attackers like to hit include Thailand, Hong Kong, China, Mexico, and Singapore, each with different banking laws and security processes in place. For some reason, fraudsters like their first hop to go to these countries, Payton said.
She added that if enterprises don't operate in any of these countries, it's good to know to put an extra flag on wire transfers if the request is for one of those countries—before equipment is purchased or leased, for example.
Britton said BEC is overwhelmingly pervasive, but it doesn't make the news like ransomware; and the bad actors know it. If an employee pays a $50,000 fake invoice, it doesn't draw as much attention, even if it does cause embarrassment to the person who was duped.
"It's an easy attack for them to be successful at," Britton said. "It's a high return on investment, low risk to them, and they are usually operating in countries or jurisdictions where law enforcement may be a little more lax and rules are a little lighter."
People are wired to be helpful and to act when there is a sense of urgency, Britton said, and cyber attackers play on that. People more times than not are unwilling accomplices.
[RELATED: 5 Emotions Used in Social Engineering Attacks]
To view the full webcast on-demand, click this link (and this is not a ransomware link, we promise).





