After a typical cyber attack perpetrated by the DarkSide ransomware group, they would laugh all the way to their crypto wallets.
After all, it was another successful attack without repercussions.
But when your attack shuts down the top fuel pipeline in the U.S. and leaves millions of Americans without fuel, you might get a little sweaty under that hacker hoodie of yours.
Chances are good that someone will be coming for you, if they can do it.
It appears someone has interfered with DarkSide's operations, and the group says that, combined with "pressure from the U.S.," is forcing it to pull the plug on its ransomware as a service (RaaS) model.
DarkSide ransomware group claims it is ceasing operations
Dark Web threat intelligence firm Intel 471 found and translated a post from DarkSide's operators on a Russian cybercrime forum.
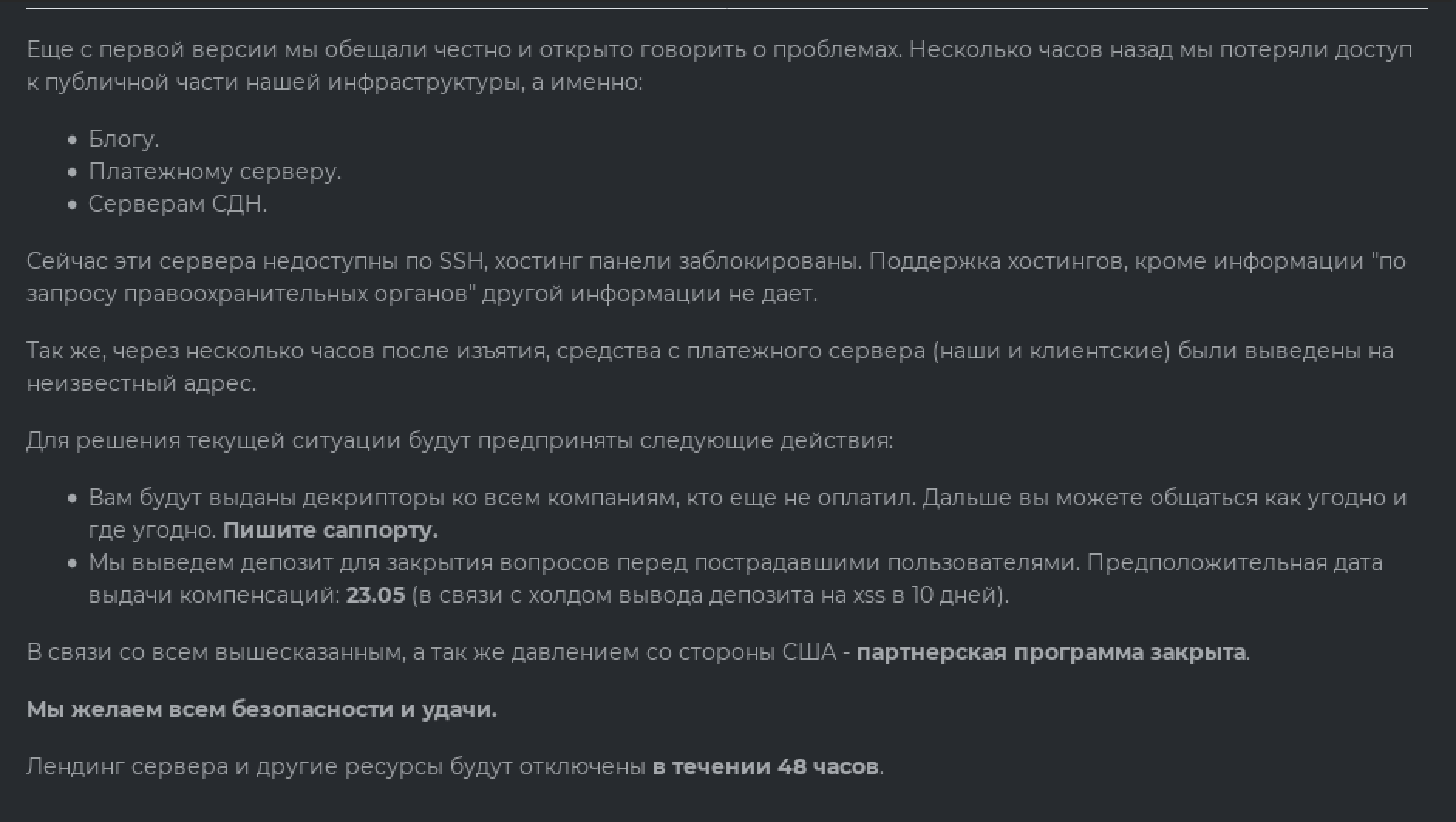
Translated in English, below, the note is to customers who use DarkSide's ransomware abilities to launch cyberattacks around the world:
"Starting from version one, we promised to speak about problems honestly and openly. A couple of hours ago, we lost access to the public part of our infrastructure, in particular to the
blog
payment server
CDN servers
At the moment, these servers cannot be accessed via SSH, and the hosting panels have been blocked.
The hosting support service doesn't provide any information except "at the request of law enforcement authorities." In addition, a couple of hours after the seizure, funds from the payment server (belonging to us and our clients) were withdrawn to an unknown account.
The following actions will be taken to solve the current issue: You will be given decryption tools for all the companies that haven't paid yet.
After that, you will be free to communicate with them wherever you want in any way you want. Contact the support service. We will withdraw the deposit to resolve the issues with all the affected users.
The approximate date of compensation is May 23 (due to the fact that the deposit is to be put on hold for 10 days on XSS).
In view of the above and due to the pressure from the US, the affiliate program is closed. Stay safe and good luck.
The landing page, servers, and other resources will be taken down within 48 hours."
The message was posted exactly one week after the DarkSide-powered ransomware attack on Colonial Pipeline.
DarkSide ransomware tried avoiding problems for itself
Following the attack on Colonial Pipeline, DarkSide ransomware operators clearly knew the magnitude of fallout from the attack could spiral back toward the cybercrime group.
A couple of days after the incident, it apologized for the consequences of its attack and claimed it was just trying to make money, not create a gas shortage. "Hey, we're not that bad," the group seemed to be saying on its blog:
"Our goal is to make money, and not creating problems for society. From today we introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future."
But now the group is, at least temporarily, in retreat. And so are others in the ransomware industry who are apparently feeling the pressure as fallout from this attack.
Intel 471 researchers explain:
"DarkSide was not the only group to make this type of announcement on May 13. Another RaaS group, Babuk, claimed it handed over the ransomware's source code to 'another team,' which would continue to develop it under a new brand. The group pledged to stay in business, continuing to run a victim name-and-shame blog, while also encouraging other ransomware gangs to switch to a private mode of operation.
Shortly after the above announcements, the administrator for one of the most popular Russian-language cybercrime forums announced an immediate ban of all ransomware-related activity on their forum.
The forum now prohibits ransomware advertising, sales, ransom negotiation services, and similar offers. Any listings that are currently on the forums will be deleted. The administrator explained the move by saying ransomware operations are becoming 'more and more toxic' and dangerous for the underground community.
That announcement caused a ripple effect on the forum, causing other well-known RaaS affiliates to make their own announcements regarding the status of their operations. One operator known to be behind the REvil ransomware program announced they would stop promoting their malware on the forum, deleting the forum thread where the service was advertised."
Researchers have previously seen these kinds of retreats by cybercriminal groups caught in the spotlight, but typically the retreat is only temporary, or new threat actors step in to fill the void left by those groups laying low for the time being.
"...a strong caveat should be applied to these developments: it's likely that these ransomware operators are trying to retreat from the spotlight more than suddenly discovering the error of their ways. A number of the operators will most likely operate in their own close-knit groups, resurfacing under new names and updated ransomware variants."
There is too much money to be made through ransomware attacks and digital extortion for these operations to voluntarily agree to shut the industry down.
Would making ransomware payments illegal do the trick? And what is it like to be an organization in the middle of a ransomware attack?
Colonial Pipeline ransomware attack: should payments be illegal?
Watch the SecureWorld LinkedIn Livestream on the attack to gain insights on both of these questions.




