Big Data is powering digital transformation initiatives around the world.
But innovating through data also creates a long list of cybersecurity and privacy challenges. Here's an idea of how that looks:
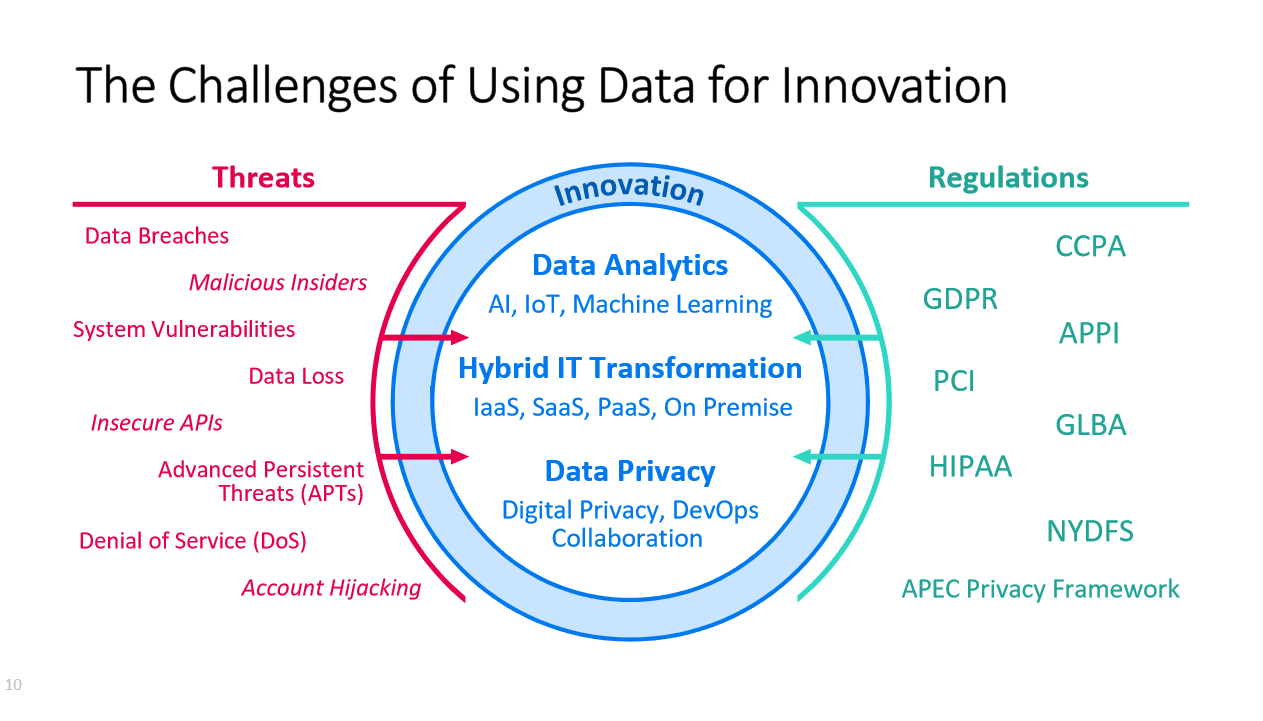
"If you look at where breaches are happening, most data breaches occur at the application level, and in the gaps between protection of data-at-rest and data-in-motion. You want to embed security into the data itself, to protect data in motion, in use, and at rest," says Carole Murphy, Global Product Senior Manager for Micro Focus Voltage. "If encrypted data is stolen in a data breach, it can’t be monetized or used on the Dark Web."
Murphy explored this topic as part of the SecureWorld web conference, Innovative Information Protection for a Data-Driven Economy, which is available on-demand.
The varying layers of encryption
What most organizations need help finding is the intersection of cybersecurity and data use. Where is that sweet spot that maximizes both?
Murphy explained the varying types of encryption which organizations use today.
"Different kinds of encryption provide different kinds of protection, and mostly, these are cumulative," she said.
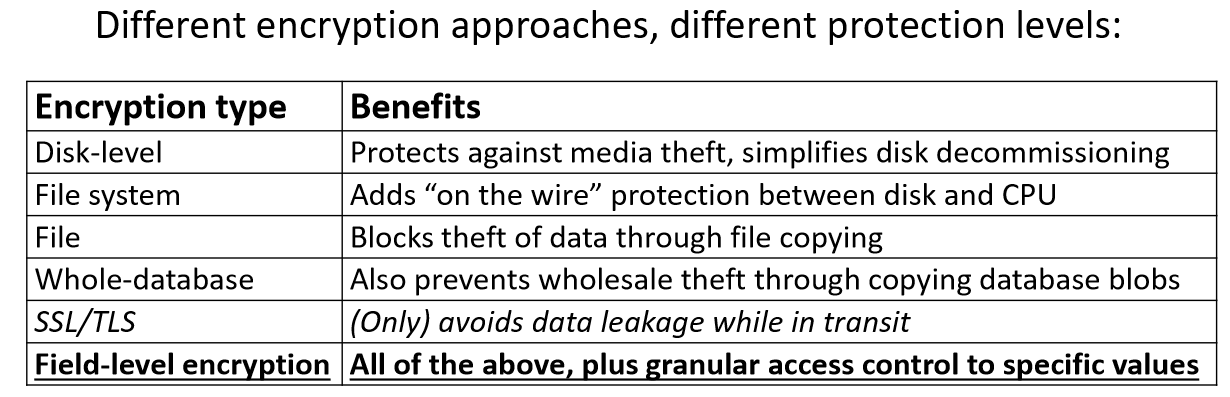
But what is most crucial when it comes to a successful data encryption strategy?
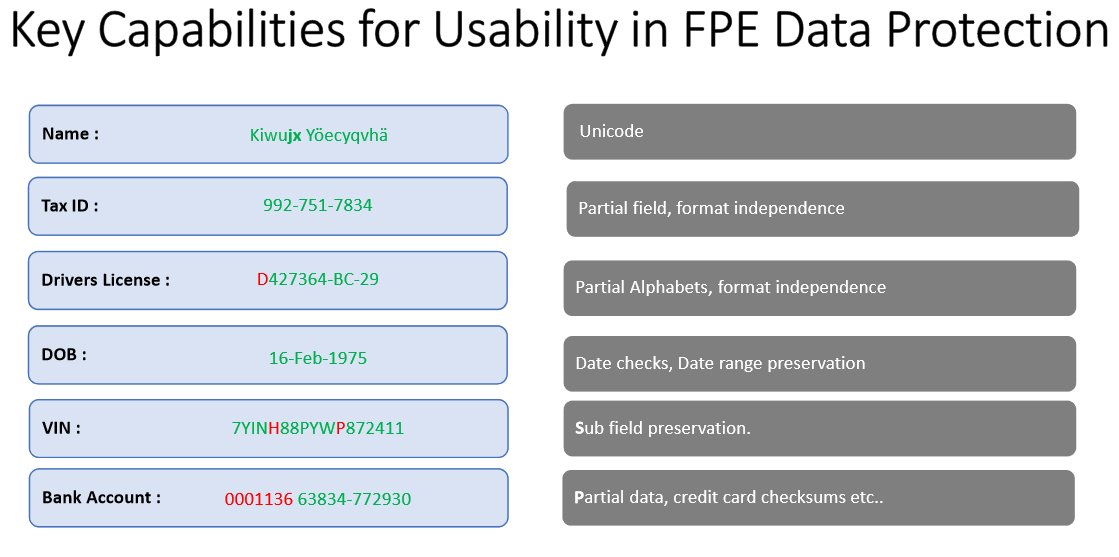
She unpacked the key capabilities for usability in FPE Data Protection. For example, it must preserve data format, and also meaning, logic, context, and relationships about the data.
HSM use is growing
Juan Asenjo, PhD, CISSP, Sr. Solutions & Partner Manager at nCipher, discussed the growth of using HSMs as part of an encryption or key management strategy that is manageable for an organization, and more organizations are realizing this:

"HSM can protect and manage the underpinning cryptographic keys, help with auditing and compliance. It can also help create that vital root of trust for safe and secure deployment as we have more IoT and other devices," Asenjo said.
"We must ensure the underpinning keys are always protected. These devices offer enhanced security and an enhanced security posture."
He also answered questions about security tools for Blockchain and many other nuances of data and encryption.
If your organization is collecting and using increasing amounts of data, then you may need help to maintain its confidentiality and integrity, and ensure compliance with data privacy requirements (such as GDPR and CCPA).
Check out the web conference, Innovative Information Protection for a Data-Driven Economy, which is available on-demand, for key takeaways in this area.




