Air-gapping a device or system is thought of as a way to isolate your device from the internet, or other public-facing networks, so that it is highly secure and untouchable to threat actors. For the most part, it's a very good way to secure your device. Though, there are exceptions.
A security researcher has discovered a workaround to air-gapped systems that involves sending Morse code signals via LED lights on network interface controller (NICs).
Dr. Mordechai Guri, the head of research and development at the Cyber Security Research Center in the Ben Gurion University of the Negev in Israel, named the method ETHERLED and recently disclosed his findings.
An NIC displays the status and activity of a device with LEDs. If malware were installed on the device, it could control the LEDs by blinking and changing colors with firmware commands. Information could then be encoded with things such as Morse code. According to Dr. Guri, a threat actor could intercept these signals from ten to hundreds of meters away.
The diagram below displays a visualization of the process:
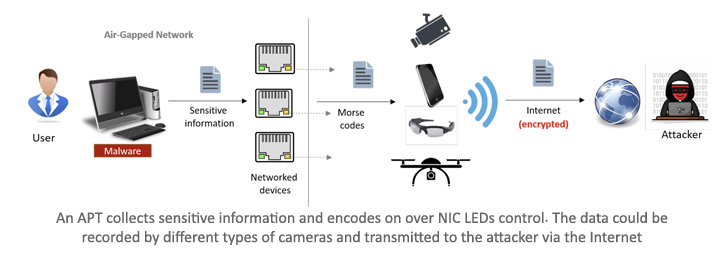
Though, just as with many other methods of targeting air-gapped devices, initial entry to the network environment is still necessary for threat actors.
Dr. Guri dives into the details of what an attack would look like in this scenario:
"At the initial phase of the attack, the adversary must execute malicious code within the targeted system to enable control of the NIC LEDs. The target might be an isolated or highly secure computer or other networked devices such as embedded systems, printers,
cameras, and any device with a wired network interface.
The infection of a device can be achieved via supply chain attacks, social engineering techniques, or the use of hardware with installed software or firmware.
At the second phase of the attack, the malicious code collects data from the compromised network. The data can be textual (e.g., user names, passwords, key-loggings) or binary (e.g., encryption keys, biometric information).
After collecting the information, the malware starts the exfiltration phase. In our case, the attack uses the optical covert channel for the data exfiltration. The malicious code uses the network card's status LEDs to encode the textual or binary information in stealth and covert ways, such as optical data modulations and Morse codes.
The attacker receives the optical signals via cameras with a line of sight with the compromised device NIC LEDs. Several types of equipment can be used in this attack model. The attack may attack video surveillance, closed-circuit TV, or IP camera positioned in a location with a line of sight with the transmitting computer. "
Dr. Guri highlights the fact that in March 2021 a group of hackers was able to successfully compromise a Silicon Valley startup that worked with security cameras. Thanks to a Check Point security report following the incident, it was determined that 150,000 IP cameras inside public organizations such as hospitals, police departments, and schools were compromised by hackers.
These cameras record the NIC LEDs so that the threat actor can decode the signals and retrieve the encoded information.
Dr. Guri's research discusses many more technical details of the exploit, including countermeasures that can be implemented to mitigate an ETHERLED attack. If you are interested, you can find his research here.




