In this case, that blue check mark next to these Twitter handles had some compromising consequences.
Hacked tweets from major Twitter accounts
What do Joe Biden, Bill Gates, Elon Musk, Apple, Barack Obama, Kanye West, Kim Kardashian West, Warren Buffett, Jeff Bezos, and Mike Bloomberg have in common?
For one, they're all verified on Twitter.
For another, all their accounts were recently hacked in a cryptocurrency cyber scam.
One by one, each account tweeted the same thing. Here's an example from Bill Gate's page:
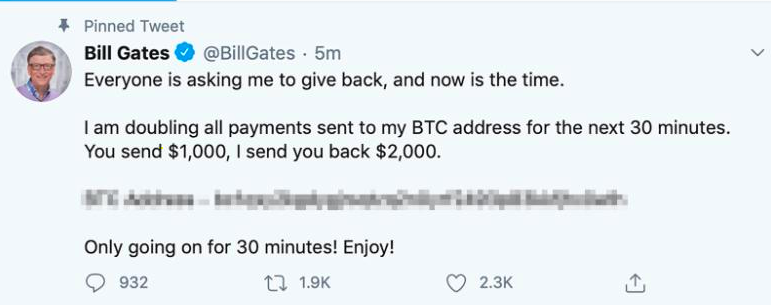
"Everyone is asking me to give back, and now is the time. I am doubling all payments sent to my BTC address for the next 30 minutes. You send $1,000, I send you back $2,000."
With the guise of "giving back" or "donating to my community" amid COVID-19, these fake tweets actually direct users to a Bitcoin wallet where the money should be sent.
How much did Bitcoin scammers make from Twitter account hack?
The wallet was only active briefly, but Tim Cotten, a Bitcoin researcher, told CNN that people fell for the double-your-money scam:
"In the hours immediately after the wallet's identification number was posted to Twitter, it received more than $100,000 worth of Bitcoins through hundreds of transactions."
Perhaps the number isn't surprising, given the massive followers these users possess on Twitter.
But with hacks like these, the danger can extend far beyond financial consequences. This social media hack burned Twitter and its users:
"The sheer number of prominent accounts impacted made it arguably the biggest security incident in Twitter's history. So many world leaders use Twitter—and some, like President Donald Trump, use it to announce major policy decisions. A hack that took over an account belonging to one of those leaders could have devastating consequences."
Multiple hacked accounts were quick to shut down the attack, including Bill Gates and Joe Biden.
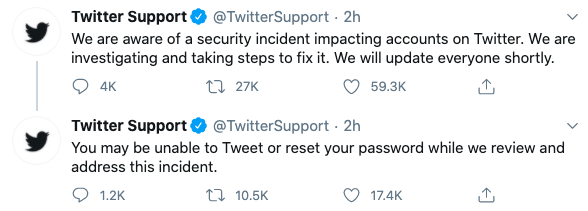
When Twitter got wind of the scam tweets, it took immediate action, locking down the accounts of verified users and tweeting these updates:
"We are aware of a security incident impacting accounts on Twitter. We are investigating and taking steps to fix it. We will update everyone shortly."
"You may be unable to Tweet or reset your password while we review and address this incident."
While the details behind these attacks are unclear, investigative agencies have already taken notice, including the FBI:
"We are aware of today's security incident involving several Twitter accounts belonging to high profile individuals," the FBI's San Francisco field office said in a statement. "The accounts appear to have been compromised in order to perpetuate cryptocurrency fraud. We advise the public not to fall victim to this scam by sending cryptocurrency or money in relation to this incident."
What part did a Twitter insider threat play in the hack?
Motherboard is reporting that this widespread takeover of prominent accounts was made possible because of an insider threat—a Twitter employee who cooperated in some way with hackers.
The question is, how?
"We used a rep that literally done all the work for us," one of the sources told Motherboard. The second source added they paid the Twitter insider. Motherboard granted the sources anonymity to speak candidly about a security incident. A Twitter spokesperson told Motherboard that the company is still investigating whether the employee hijacked the accounts themselves or gave hackers access to the tool."
Previous insider threat case at Twitter
If this was related to an insider threat or rogue employee at Twitter, the company may need to re-examine its insider threat program.
Last year, SecureWorld News reported on the case of Ali Alzabarah, a 35-year-old citizen of Saudi Arabia and a Twitter reliability engineer.
Alzabarah wrote to a Saudi government official that his greatest achievement was not his career, it was being an insider threat at Twitter on behalf of the Saudi government.
"Today I became officially a member of the technical team at Twitter, this is the fifth tier out of six for engineers in companies in the Silicon Valley... My happiness is unimaginable and wanted to share with you the good news... thank you for supporting me and everything... As much as I am happy for the position, I am happier with and very proud of my work with you."
The U.S. Department of Justice explains what the reliability engineer was doing:
"Specifically, representatives of the Kingdom of Saudi Arabia and the Saudi Royal Family sought the private information of Twitter users who had been critical of the regime."
Who would have more access to Twitter users than a Twitter employee?
And he did not work alone. He worked in cooperation with another rogue Twitter employee, 41-year-old Ahmad Abouammo, who was a media partnerships manager for Twitter, responsible for the Middle East North Africa (MENA) region.
The FBI describes his role at the company: "[Abouammo]... was involved in assisting notable accounts of public interest, brands, journalists, and celebrities for the MENA region with content, Twitter strategy and sharing best practices."
And the FBI says Abouammo "had access to proprietary and confidential Twitter information, including information about Twitter users, including the user-provided email addresses, birthdates, phone number and IP addresses."
According to the DOJ, the two former Twitter employees helped track down critics of the Saudi Royal Family through their tweets, IP addresses, and logins.
Read Insider Threat Case: Twitter Employees Bribed by Saudis for more.
Were Twitter employees social engineered?
As the Twitter investigation continues, the company is (surprise!) tweeting about the incident, and it's floating the idea that its employees may have unwittingly helped the cybercriminals after a social engineering attack.
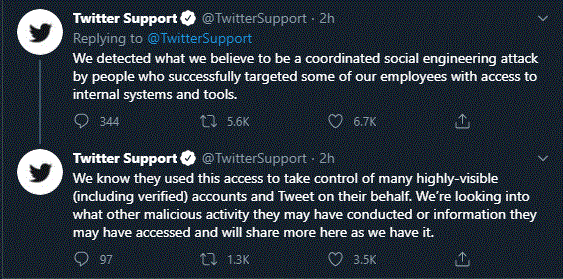
"We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and controls."
We'll see where the investigation goes next, and we'll be sure to tweet about it.





