The United States Drug Enforcement Agency (DEA) is currently investigating claims that threat actors gained unauthorized access to a portal connected to 16 different federal law enforcement databases, according to KrebsOnSecurity.
The incident is allegedly connected to a cybercrime group known for harassment, whose members impersonate police officers and government officials to gather personal information on their victims.
Earlier this week, Brian Krebs reports the hackers obtained a username and password for the Law Enforcement Inquiry and Alerts (LEIA) system managed by the DEA.
Yes, you read that correctly: a simple login was used by threat actors to access a federal law enforcement database.
LEIA "provides federated search capabilities," which includes classified sensitive data pertaining to the DEA. LEIA also has access to the National Seizure System (NSS), which the DEA uses to identify property purchased with illicit proceeds.
The hackers shared this screenshot of the LEIA system:
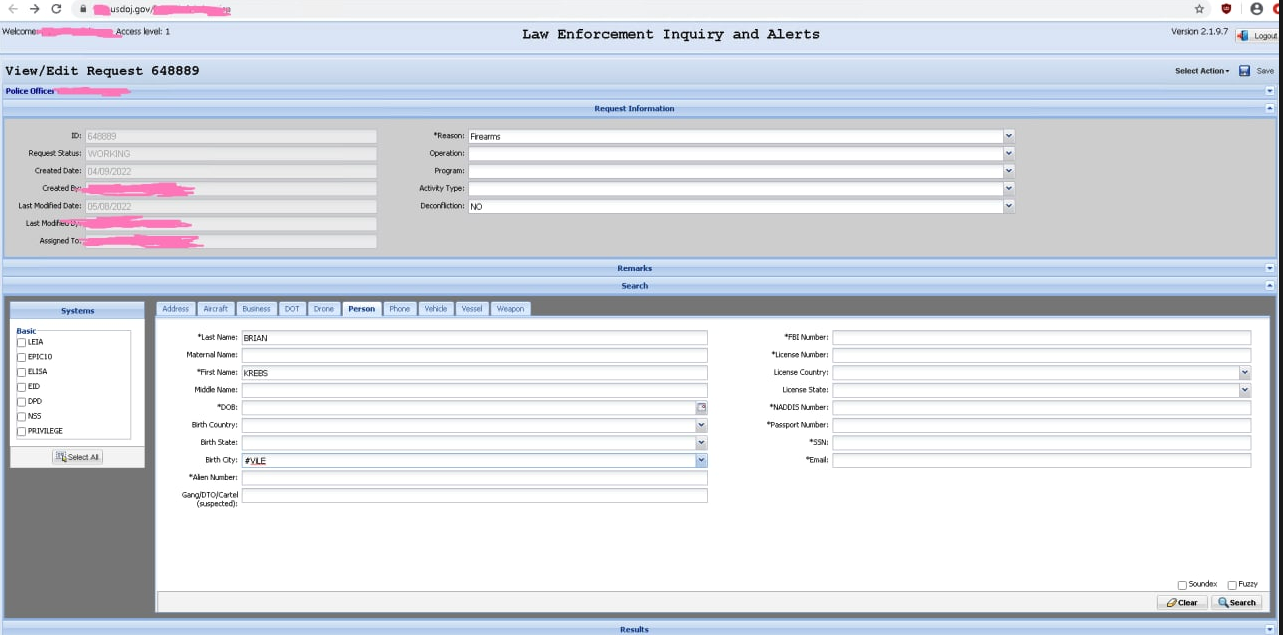
Nicholas Weaver, a researcher for the International Computer Science Institute at University of California, Berkeley, says the screenshot is proof the hackers do have access, but it's more than that. He says they could also submit false records to law enforcement and intelligence agency databases:
"I don't think these [people] realize what they got, how much money the cartels would pay for access to this. Especially because as a cartel you don't search for yourself, you search for your enemies, so that even if it's discovered, there is no loss to you of putting things ONTO the DEA's radar."
Krebs said he believes this incident should be treated as a serious warning for politicians in D.C. to act on cybersecurity, and that there really needs be a now-or-never approach. He concludes his blog with this:
"The United States government is in urgent need of leadership on cybersecurity at the executive branch level—preferably someone who has the authority and political will to eventually disconnect any federal government agency data portals that fail to enforce strong, multi-factor authentication.
I realize this may be far more complex than it sounds, particularly when it comes to authenticating law enforcement personnel who access these systems without the benefit of a PIV card or government-issued device (state and local authorities, for example). It's not going to be as simple as just turning on multi-factor authentication for every user, thanks in part to a broad diversity of technologies being used across the law enforcement landscape.
But when hackers can plunder 16 law enforcement databases, arbitrarily send out law enforcement alerts for specific people or vehicles, or potentially disrupt ongoing law enforcement operations—all because someone stole, found or bought a username and password—it's time for drastic measures."
For more information, see the original post from KrebsOnSecurity, DEA Investigating Breach of Law Enforcement Data Portal.





