The FBI, U.S. Department of Health and Human Services, and U.S. Cybersecurity Infrastructure Security Agency (CISA) have issued a joint cybersecurity advisory with information about "Daixin Team," a cybercrime group actively targeting U.S. businesses with ransomware and data extortion operations.
The biggest target is the Healthcare and Public Health (HPH) sector, according to the advisory. "As of October 2022, per FBI Internet Crime Complaint Center (IC3) data, specifically victim reports across all 16 critical infrastructure sectors, the HPH Sector accounts for 25 percent of ransomware complaints."
The report continues:
Daixin Team is a ransomware and data extortion group that has targeted the HPH sector with ransomware and data extortion operations since at least June 2022. Since then, Daixin Team cybercrime actors have caused ransomware incidents at multiple HPH sector organizations where
they have:
- Deployed ransomware to encrypt servers responsible for healthcare services—including electronic health records services, diagnostics services, imaging services, and intranet services; and/or
- Exfiltrated personal identifiable information (PII) and patient health information (PHI) and threatened to release the information if a ransom is not paid
Virtual private networks (VPN) servers are the gateway for Daixin actors, who have exploited unpatched vulnerabilities in organizations' VPN servers, or, in one case, previously compromised credentials were used to access a legacy VPN server without multifactor authentication (MFA) enabled.
Once in, Daixin Team threat actors use Secure Shell and Remote Desktop Protocol (RDP) to move laterally through systems, gaining privileged account access and resetting passwords on servers. The advisory credits third-party providers for identifying Babuk Locker as the source code for the Daixin actors' ransomware.
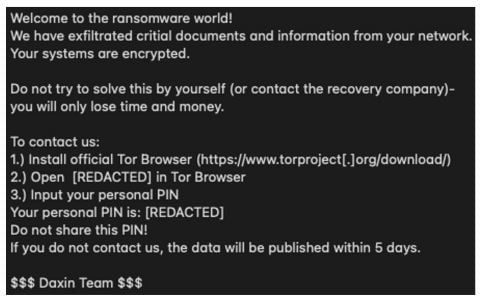 Ransomware note from Daixin Team
Ransomware note from Daixin Team
See the advisory for a complete list of techniques and use cases, including reconnaissance, initial access, persistence, credential access, lateral movement, exfiltration, and impact.
Additional details from the advisory:
"In addition to deploying ransomware, Daixin actors have exfiltrated data from victim systems. In one confirmed compromise, the actors used Rclone—an open-source program to manage files on cloud storage—to exfiltrate data to a dedicated virtual private server (VPS). In another compromise, the actors used Ngrok—a reverse proxy tool for proxying an internal service out onto an Ngrok domain—for data exfiltration."
The FBI is seeking any additional information from victims of attacks, including logs showing communications to and from foreign IP addresses, sample ransom notes, communications from Daixin Group actors, Bitcoin wallet information, decryptor files, and/or a benign sample of an encrypted file.





