The new cybercrime gang on the block turned out to also be the new kids on the block—literally.
The Lapsus$ group has made a huge splash in 2022 with some of the most eventful cyberattacks we've seen in recent memory.
Their first notable attack occurred in December 2021, when they hacked Brazil's Ministry of Health. Since then, the gang has managed to pull off hacks on some of the largest tech companies in the world, including NVIDIA, Samsung, Ubisoft, Microsoft, Okta, and most recently IT firm Globant.
What has made these attacks intriguing for many is that the group has been leaking screenshots of source code and internal documents for some of these organizations, putting business leaders in a difficult position: cooperate with these criminals or risk more data being exposed.
And in an exciting twist to the story, Bloomberg reported that one of the masterminds behind Lapsus$ was actually a 16-year-old boy living with his mother in England.
As it turns out, most of the gang's associates are also teenagers. But after hacking these giant tech companies, law enforcement took notice. London police arrested seven individuals, all teenagers, for their crimes. All have since been released, but this story is far from over.
Teen cybercriminals target security firms
The arrests were made after the Okta incident, which affected 366 of Okta's customers and sparked some controversy over how the company handled messaging around the incident.
After the arrests, an associate of Lapsus$ shared on Telegram that some of its members would be on "vacation" until March 30. At the time, security researchers believed this indicated the group would be winding down with arrests being made, and that "vacation" really meant jail.
But it looks like some members truly might have just been on spring break, as this message was shared to their 54,000 followers on Telegram: "We are officially back from a vacation."
News broke this morning that Lapsus$ hacked IT firm Globant and leaked roughly 70 GB of source code along with administrator passwords.
They also posted a screenshot the group claims to be of an archived directory, containing folder names that may be company customers:
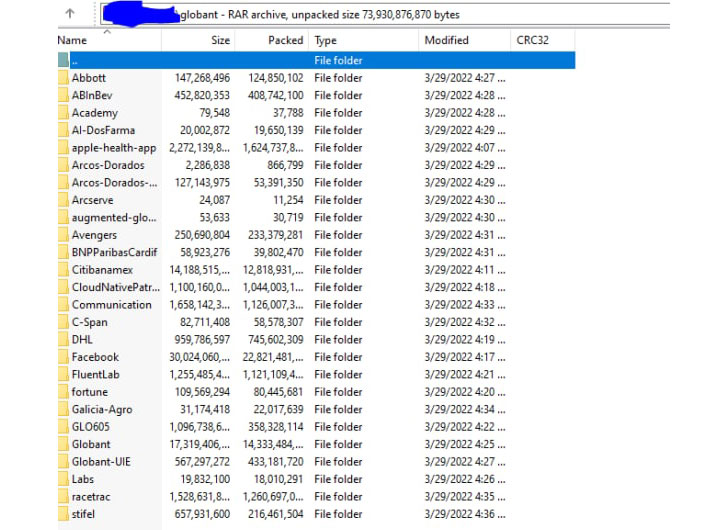
VX Underground, a malware research group, shared that Lapsus$ targeted the company because of its "poor security practices in use" and that the passwords were easily guessable and reused multiple times. Here is a screenshot of one of the messages the group posted:
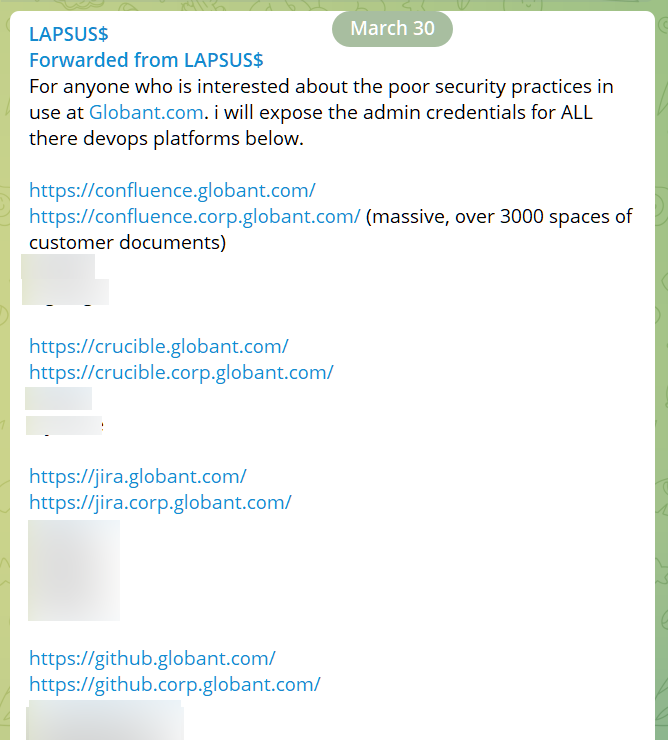
This Globant incident will likely not be the last we hear from Lapsus$. Despite the arrests, security researchers believe there are affiliates of the cybercrime group all over the world, as members on the Telegram channel speak English, Russian, Turkish, German, and Portuguese.
Follow SecureWorld News for more reporting on cybersecurity and cybercrime.





