The Lazarus Group, a North Korean cybercriminal organization known for its cyber espionage and financially motivated attacks, has been observed shifting targets and refining techniques in their campaign dubbed "DeathNote," according to a recent report by cybersecurity firm Kaspersky.
The campaign, also known as Operation DreamJob or NukeSped, has been tracked by Kaspersky since 2019, and the findings reveal significant changes in the threat actor's targets and infection vectors.
According to the report, the campaign initially used decoy documents related to cryptocurrency, but in April 2020, a shift in targets was observed towards the automotive and academic sectors in eastern Europe, which are connected to the defense industry.
The decoy documents were updated to show job descriptions related to defense contractors and diplomatic services. The infection chain was also refined, with the use of trojanized open-source PDF viewer software in addition to the remote template injection technique in weaponized documents.
Seongsu Park, Senior Security Researcher at Kaspersky and author of the report, shared what the infection chain looks like:
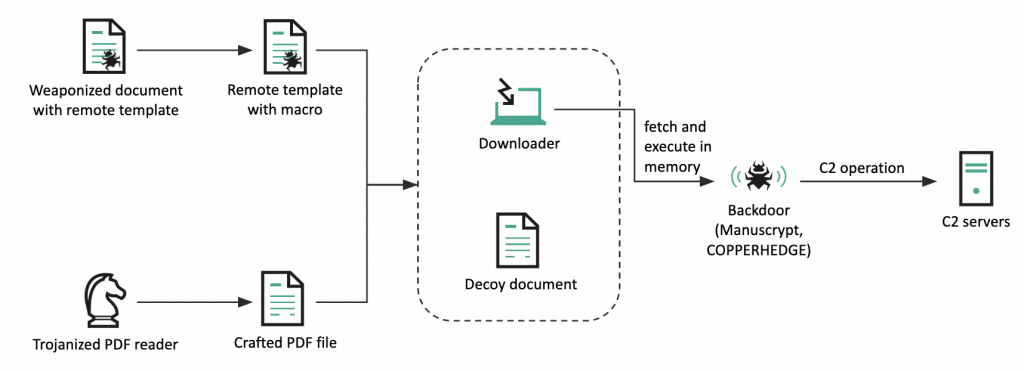
In the report, Park said, "Our analysis of the DeathNote cluster reveals a rapid evolution in its tactics, techniques, and procedures over the years." The campaign has demonstrated an ability to adapt and refine its methods to target different sectors and geographies, leveraging legitimate software and trojanized PDF viewer software to gain unauthorized access and collect victim's information.
The Lazarus Group's DeathNote campaign also infiltrated an IT company in Europe that offers network device and server monitoring solutions, as well as targeted multiple victims in South Korea, Latin America, and Africa.
Additionally, the campaign utilized legitimate security software commonly used in South Korea to spread downloader malware to several victims in the region. These tactics demonstrate the group's adaptability and persistence in targeting a diverse range of industries and regions.
The DeathNote campaign highlights the persistent and evolving nature of advanced persistent threat (APT) actors. Organizations must remain vigilant and implement strong security measures to defend against such threats. Kaspersky's advisory serves as a reminder for the need to stay informed about the latest threats and to continuously update defenses to protect against evolving cyber threats.
Read the report from Kaspersky, Following the Lazarus group by tracking DeathNote campaign, for more information.
Subscribe to SecureWorld News for more stories related to cybersecurity.





