Security researchers are some of the unsung heroes within the cybersecurity field. They are the ones who look for and discover vulnerabilities before anyone else in the world knows about them.
However, because they are heroes, they are also targets.
Google's Threat Analysis Group (TAG) has been working for several months to try to identify who is behind an ongoing campaign targeting security researchers, specifically those who work on vulnerability research and development at a variety of organizations.
Google's TAG team has identified the threat actors behind this campaign as a "government-backed entity based in North Korea."
How is North Korea targeting security researchers?
The North Korea based threat actors are using a number of different strategies to target security researchers. Let's take a look at four of them.
1. One of the strategies Google's TAG team says the nation-state hackers are using is imitating those they want to attack:
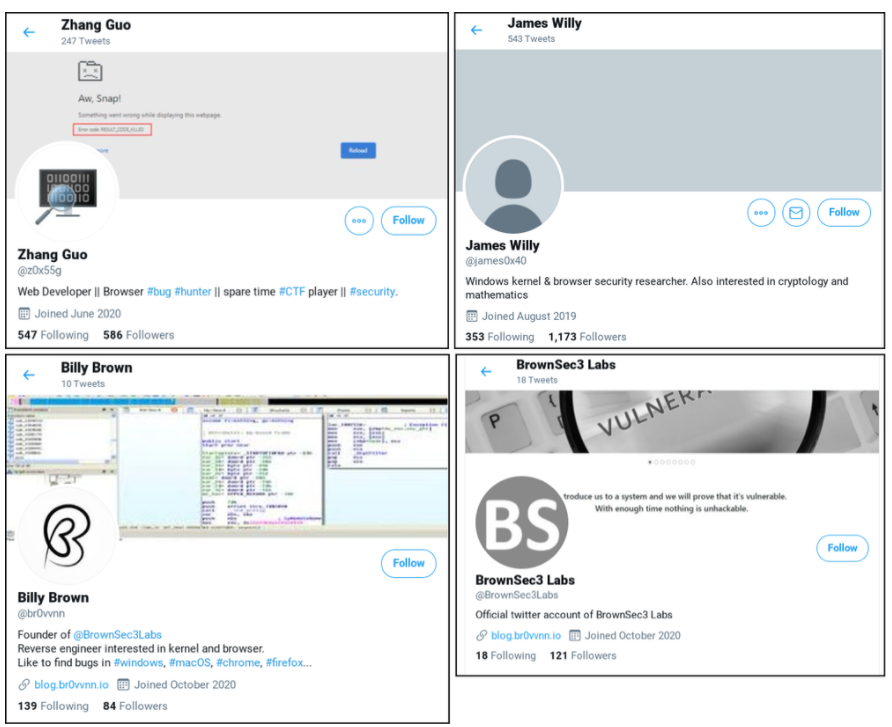
"In order to build credibility and connect with security researchers, the actors established a research blog and multiple Twitter profiles to interact with potential targets.
They've used these Twitter profiles for posting links to their blog, posting videos of their claimed exploits and for amplifying and retweeting posts from other accounts that they control.
Their blog contains write-ups and analysis of vulnerabilities that have been publicly disclosed, including 'guest' posts from unwitting legitimate security researchers, likely in an attempt to build additional credibility with other security researchers."
Here is a look at some of the profiles the threat actors have been controlling:
2. Another strategy North Korean hackers are using against security researchers is faking success stories. The research community caught on to this tactic:
"On Jan 14, 2021, the actors shared via Twitter a YouTube video they uploaded that proclaimed to exploit CVE-2021-1647, a recently patched Windows Defender vulnerability. In the video, they purported to show a successful working exploit that spawns a cmd.exe shell, but a careful review of the video shows the exploit is fake.
Multiple comments on YouTube identified that the video was faked and that there was not a working exploit demonstrated. After these comments were made, the actors used a second Twitter account (that they control) to retweet the original post and claim that it was 'not a fake video.'"
Can security researchers be socially engineered?
Google's TAG team has also identified other strategies in which the actors have been targeting security researchers.
3. A third technique in play relies on social engineering, where the bad actors ask a researcher if they want to collaborate on vulnerability research and then provide a Visual Studio Project. It's an effort at establishing a backdoor:
"Within the Visual Studio Project would be source code for exploiting the vulnerability, as well as an additional DLL that would be executed through Visual Studio Build Events. The DLL is custom malware that would immediately begin communicating with actor-controlled C2 domains."
Microsoft has attributed the recently exposed long-con social engineering of vulnerability researchers to the North Korean group Microsoft calls “Zinc” and most others know as the Lazarus Group.
4. A fourth methodology, according to Google TAG, was making the fake research blog into a sort of honeypot, which attracted researchers and served up malware in a backdoor attack:
"In each of these cases, the researchers have followed a link on Twitter to a write-up hosted on blog.br0vvnn[.]io, and shortly thereafter, a malicious service was installed on the researcher's system and an in-memory backdoor would begin beaconing to an actor-owned command and control server. At the time of these visits, the victim systems were running fully patched and up-to-date Windows 10 and Chrome browser versions."
The TAG team notes that Google has been unable to confirm the mechanism of compromise.
They also say the actors are using multiple platforms to communicate with targets, including Twitter, LinkedIn, Telegram, Discord, Keybase, and email.
Google's TAG team discovery: cyberattack motive
News of TAG's findings has quickly spread through the cybersecurity community, with warnings about interacting with unknown accounts and people online.
The Global Vice President at New Net Technologies, Dirk Schrader, shared his thoughts on what the TAG team uncovered:
"For this, one has to keep in mind the process of a responsible disclosure used by most security researchers. A bit simplified, they inform the vendor about their findings, the vendor verifies the findings and fixes the bug, and with the release of the patch the researcher gets credit. Google's policy of a 90-day disclosure deadline tries to limit this period as for some vendors it can take ages.
And exactly there is the catch, when having early access to newly found, fresh vulnerabilities, the APT groups leap forward in their capabilities to attack networks and systems. That is why it is critical to learn as much as possible about this social engineering attempt because it will serve as a template for others, similar to the SolarWinds attack.
Cyber crooks are trying to make inroads into software stacks, vendors' update processes, and sources of vulnerability research, and all this should be seen as a warning sign for the next level of cyber warfare.
As much as vendors advocate cybersecurity and resilience to their customer base and the market, they themselves (including my company, NNT) have to keep an eye on our processes and their outcome, on our own cyber resilience."
To see a full list of accounts and aliases used by threat actors, as well as other information regarding this situation, read the TAG team's updates on the campaign targeting security researchers.