Threat actors are constantly forced to adapt their techniques to advancing technologies, and security teams and tools must pivot, as well.
It is a cycle that sometimes puts your end-users in the middle of this back and forth battle.
We are seeing a prime example of this in a newly discovered phishing campaign, where a threat actor is inverting the colors of an image in an attempt to deceive scanning engines.
Phishing campaign inverts images
Phishing attacks reached an all-time high earlier this year; however, a huge number of these attacks are stopped before ever reaching an inbox.
At least part of this is because technologies, like detection engines, are getting better at picking up on malicious clues, links, and other red flags.
It is challenging for threat actors to create a phishing website that bypasses the detection engine while also portraying the targeted site accurately enough to fool potential victims.
However, security researchers at WMC Global report that a new "bot avoidance mechanism" is being used on some Microsoft Office 365 credential phishing websites. Here is how they describe the technique:
"Because image recognition software is improving and becoming more accurate, this new technique aims to deceive scanning engines by inverting the colors of the image, causing the image hash to differ from the original. This technique can hinder the software's ability to flag this image altogether.
However, a victim visiting the website would likely recognize that the inverted picture is illegitimate and exit the website. As a result, the threat actor has stored the inverted image and, within the index.php code, has used a CSS method to revert the color of the image to its original state.
This approach results in the final website's appearing legitimate to users who visit, while crawlers and scanning engines are highly unlikely to detect the image as being an inverted copy of the Office365 background."
See the original image:
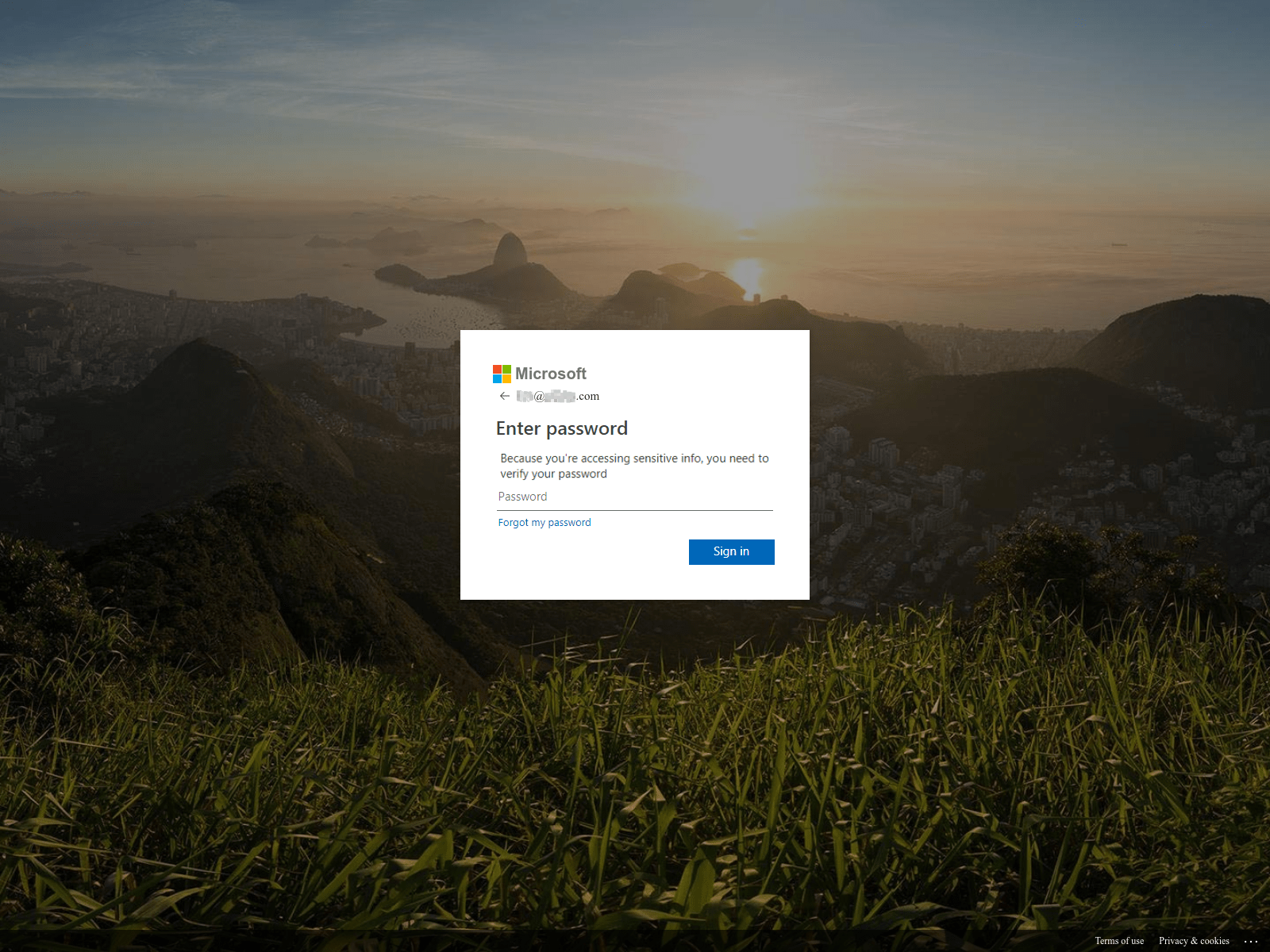
And the inverted image:

Attack appears to by cybercrime-as-a-service model
At this point, it seems like this attack method is in limited use, but it appears to be available for purchase on the Dark Web.
Here is what WMC Global said about this phishing method:
"WMC Global threat analysts attribute the use of this method to a single threat actor selling the phishing kit to multiple users."
The cybercrime-as-a-service model continues to gain popularity.
For more information on this new phishing campaign, check out WMC Global's report on image inversion.





