It is a key piece of America's critical infrastructure that helps people go places. And it helps the United States defend itself.
Colonial Pipeline delivers about 40% of the fuel consumed by the east coast market. This includes diesel fuel, jet fuel for commercial aviation, home heating oil, and fuels for the U.S. military.
A ransomware attack against the pipeline's owner shut the pipeline down last Friday.
Now, President Biden has issued an Emergency Waiver that will make it easier for trucks and ships to transport more oil and allow those involved to work longer hours doing it. This is oil that would normally flow through the pipeline.
The ransomware attack on Colonial Pipeline and the shutdown that followed is a reminder of how vulnerable critical infrastructure is to cyberattacks:
"This was not a minor target," says Amy Myers Jaffe, a long-time energy researcher and author of Energy's Digital Future. "Colonial Pipeline is ultimately the jugular of the U.S. pipeline system. It's the most significant, successful attack on energy infrastructure we know of in the United States. We're lucky if there are no consequences, but it's a definite alarm bell," she told Politico.
Here is a map of the pipeline's mainlines, which transport more than 100 million gallons of product every day. The pipeline starts in Houston, and the fuels are sourced from 30 refineries.
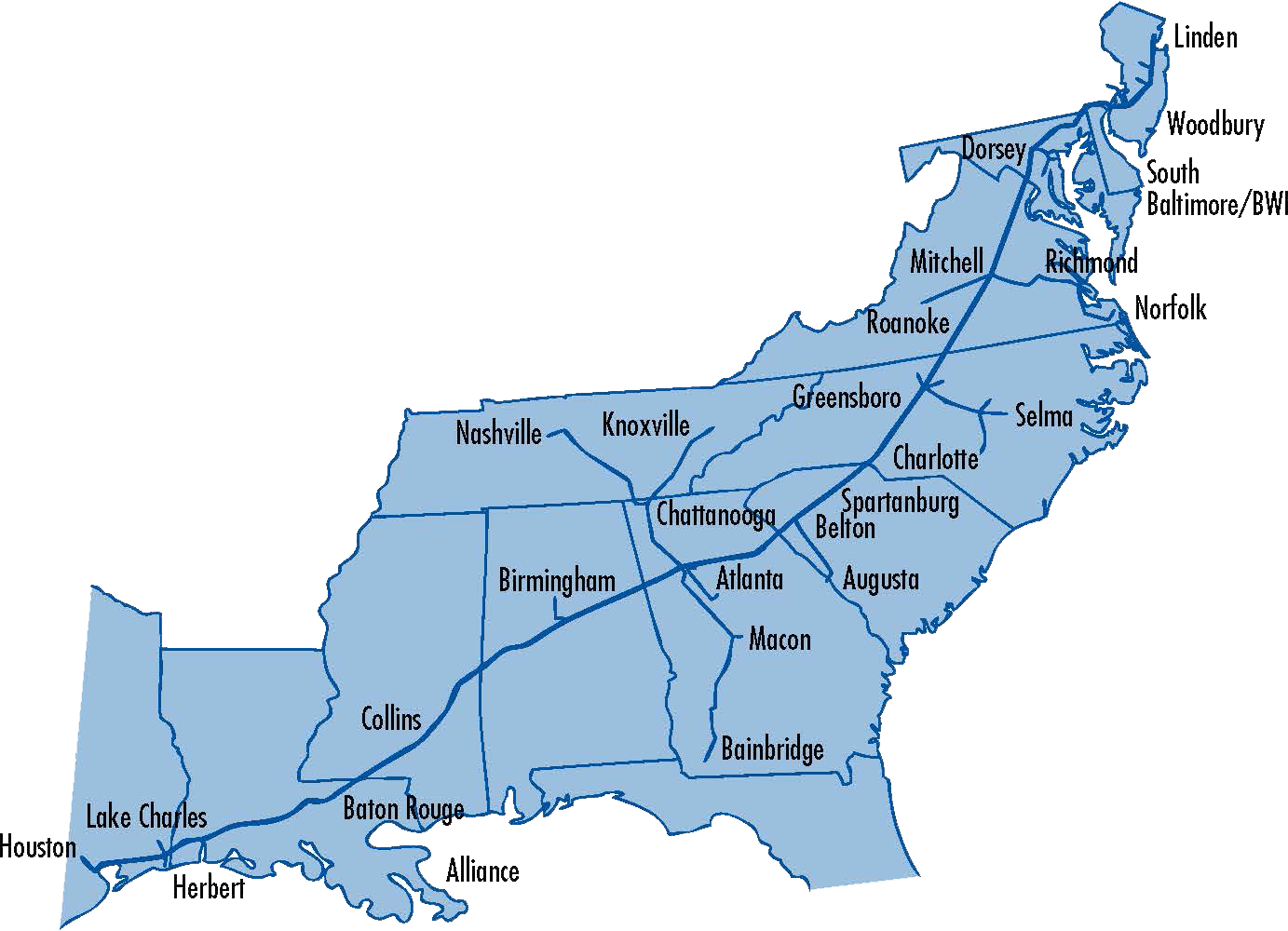
Let's look at what we know about the ransomware attack so far and the speculation around who is behind it.
Oil pipeline cyberattack timeline
Friday - ransomware hits Colonial Pipeline systems:
"On May 7, the Colonial Pipeline Company learned it was the victim of a cybersecurity attack. We have since determined that this incident involves ransomware. In response, we proactively took certain systems offline to contain the threat, which has temporarily halted all pipeline operations and affected some of our IT systems."
The incident response continued throughout the weekend.
Sunday evening, May 9 - the company says the mainlines remain offline:
"The Colonial Pipeline operations team is developing a system restart plan. While our mainlines (Lines 1, 2, 3 and 4) remain offline, some smaller lateral lines between terminals and delivery points are now operational. We are in the process of restoring service to other laterals and will bring our full system back online only when we believe it is safe to do so, and in full compliance with the approval of all federal regulations."
Questions linger about whether the operational technology (OT) that automates the pipeline was directly attacked or impacted by the ransomware attack. Automation is required to run a pipeline like Colonial's:
"Pumping different refined products along the entire length of Colonial safely and efficiently requires sophisticated, automated systems. Operating without all of them functioning is extremely challenging, according to Niyo Pearson, an oil and gas adviser for Cynalytica, told Bloomberg.
He pointed in particular to Colonial's technology regulating the pressure of gas used to push liquids through the pipe.
That 'is the brains of the system,' Pearson said. 'It controls the settings on the pipeline, what the pressure is, remote operation of valves.'"
Even if these systems were unaffected by the attack, imagine if the company's billing system or delivery reports were compromised by the ransomware. It might be impossible for Colonial Pipeline to get paid for any deliveries if that were the case.
And now, Bloomberg is reporting that the criminals behind the attack are threatening to publish data they stole from the company unless a ransom is paid:
"The intruders... took nearly 100 gigabytes of data out of the Alpharetta, Georgia-based company's network in just two hours on Thursday, two people involved in Colonial's investigation said."
Oil pipeline ransomware attack: who was behind it?
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued a rare weekend update regarding the Colonial Pipeline attack.
We are aware of the Colonial Pipeline ransomware incident. We are engaged with Colonial and our interagency partners regarding the situation. (1/3) pic.twitter.com/8YV7qEHfnc
— Cybersecurity and Infrastructure Security Agency (@CISAgov) May 8, 2021
Although there is no official attribution for the attack, yet, Russia-based criminal hacking group DarkSide is claiming responsibility. And here's a twist: It is also apologizing at the same time, including this message which NBC News found on the group's website:
"We are apolitical, we do not participate in geopolitics, do not need to tie us with a defined goverment and look for other our motives," the gang posted, misspelling 'government.'
In other words, the group is claiming they are not backed by the Russian government. But talk is cheap.
Dmitri Alperovitch is the former CTO and Co-founder of cybersecurity vendor CrowdStrike. He tweeted that this attack will very likely have implications for international relations:
So a ransomware group we believe is operating (and likely harbored) by Russia has shutdown a company that is moving 45% of petroleum supplying the East Coast.
— Dmitri Alperovitch (@DAlperovitch) May 8, 2021
Is it a criminal act? Sure.
Does it have huge natsec implications, not least on US-Russia relations? Undoubtedly
Just when you think ransomware attacks can't get any more significant, they do. And how much of that is driven by nation-state actors?
Alperovitch also has a very telling tweet pinned at the top of his Twitter account:
"As I've said before - We don't have a cyber problem, we have a China, Russia, Iran and North Korea problem."
And when it comes to Russia, a cyberwar is inevitable, according to Margarita Simonyan, Editor in Chief of the state-funded Russian media outlets RT and Sputnik.
This is what she said just a couple of weeks ago in a presentation:
"War [with the U.S.] is inevitable. I do not believe that this will be a large-scale hot war, like World War II, and I do not believe that there will be a long Cold War. It will be a war of the third type: the cyberwar.
Could this be the first shot fired? Some would say that happened long ago.



