The threat landscape is constantly evolving in cybersecurity. Hackers come up with a new attack method, organizations respond and implement new defenses, and then another hacker figures out a work around to the new defenses. It is quite the interesting cycle.
When it comes to ransomware, cybercriminals are often thinking of new ways to pressure, or shame, their victims into paying the ransom.
In a recent incident, the Allison Inn & Spa, a luxurious resort in Newberg, Oregon, was victim to an unusual ransomware attack that left employees' and guests' personal information exposed on a public facing website. Cybercriminals from the ALPHV/BlackCat ransomware gang orchestrated the attack.
But what about this incident is unusual?
The ALPHV/BlackCat gang typically publishes stolen information on the Dark Web—as do most ransomware operations—but decided it would be beneficial to make all of that data easily accessible to anyone who was curious. Brian Krebs shared a screenshot of what the ALPHV website looks like and how easy it is to search for information:
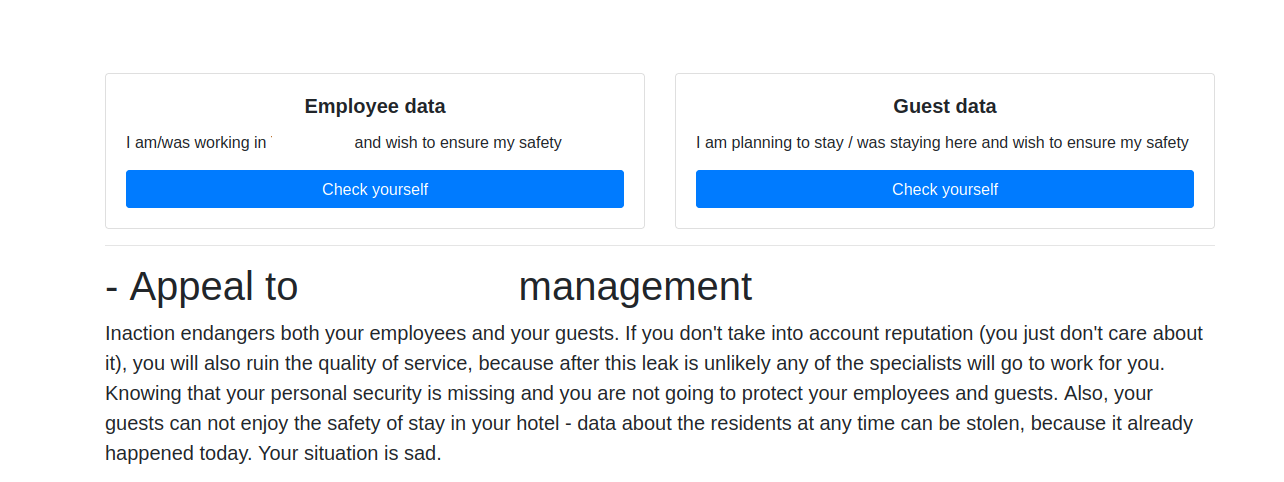
The site lists data of 1,500 employees and more than 2,500 guests, including dates that guests stayed, employees' birthdays, phone numbers, and Social Security numbers.
Brett Callow, a threat analyst for cybersecurity firm Emsisoft, discussed what he described as a "cunning" ransomware attack and why ALPHV posted the stolen information publicly:
"It's not a new strategy. It's just the way they are implementing it that is new… by putting it on the public internet in an easily searchable form. As far as I'm aware this hasn’t been done before.
They're likely doing this to see how much it moves the needle in their favor. Their intention may not simply be to try to squeeze the money out of The Allison. It may also be to pressure their future victims who look at what happened to the Allison and think, I don't want to go through that."
It will be interesting to see if the ALPHV gang continues to use this pressure tactic with all of its ransomware attacks, as this is likely a test run to see if it works.
However, Callow says there may be a silver lining to this incident:
"On a positive note, stunts like this mean people may actually find out that their PI has been compromised. Cl0p [ransomware gang] emailed my wife last year. The company that lost her data still hasn't made any public disclosure or notified the people who were impacted (at least, she hasn't heard from the company.)"
Although it's unfortunate that some people have their personal data exposed in such a public way, it would be nice to at least know that your information is out there; that way, you can be on the lookout for any phishing scams, freeze your credit, or take other defensive actions against cybercrime.





