Phishing attacks have steadily been on the rise, and according to Proofpoint's 2021 State of the Phish Report, over half of all participants reported receiving a successful phishing attack in 2020. Because attackers evoke strong emotions to try to trick users into clicking on phishing campaigns, it's important for organizations to develop a proactive, holistic strategy to keep their users safe from phishing attacks in and out of the workplace.
In this blog, we'll focus on some common phishing campaigns that our threat intelligence has seen in the wild, and the lessons your users can take away from these and other materials in our latest Phishing Awareness Kit.
Criminals use departmental reputation to trick users into trusting phishing lures
People work remotely now more than ever, and they are bombarded by more emails than before. Employees tend to have their guard up when receiving emails from external sites and check the reputation of a link before clicking on it. However, they will likely trust internal emails from cross-functional departments—especially from Human Resources.
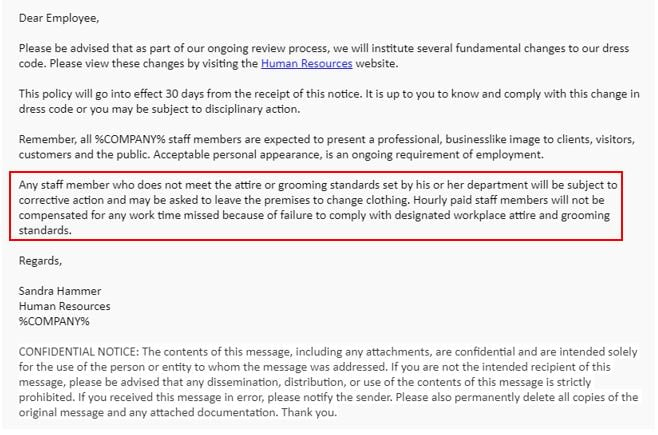 Fig. 1: Attackers use the status of HR to convince users to follow-through with the requested action.
Fig. 1: Attackers use the status of HR to convince users to follow-through with the requested action.
The email above includes a sample simulated phishing email "from HR" that looks legitimate… but what makes this email so tricky?
First, the tone and content of the email is professionally serious, discussing an "ongoing review process" and threatening employees with potential "disciplinary action." Next, it draws users' curiosities in with emotionally charged phrases like "corrective action" and "asked to leave the premises," and even mentions the failure to be compensated for missed work for hourly employees who don't comply with the dress code. For busy employees who might check these messages on their phone in between meetings, they will want to comply with company regulations to avoid getting reprimanded. Since the body of the email sounds legitimate and includes a time-sensitive period of 30 days, it's easy for users to click on the link for the HR website without hovering over it first. If the user hovered over the link, they would notice that the URL address in the email does not match any websites related to their organization. This can indicate potentially malicious sites and loss of data.
Criminals attack people by promising fake package information
With people working from home, they are more likely to order products online and anticipate receiving package notifications on their work and personal devices (which are also linked to corporate accounts). Attackers know this and have capitalized on the emotional gratification of online shopping to further their nefarious crimes.
In the image below, this cybercriminal offers enticing data of activity at each stage of the delivery process. Because users are given such detailed information up front, they might easily click on the link based on piqued curiosity and eagerness to receive their items. Additionally, because the delivery announcement mentions "Important Delivery Information" in bold and at the top, it adds a sense of urgency that will also prompt users to click on the tracking details link.
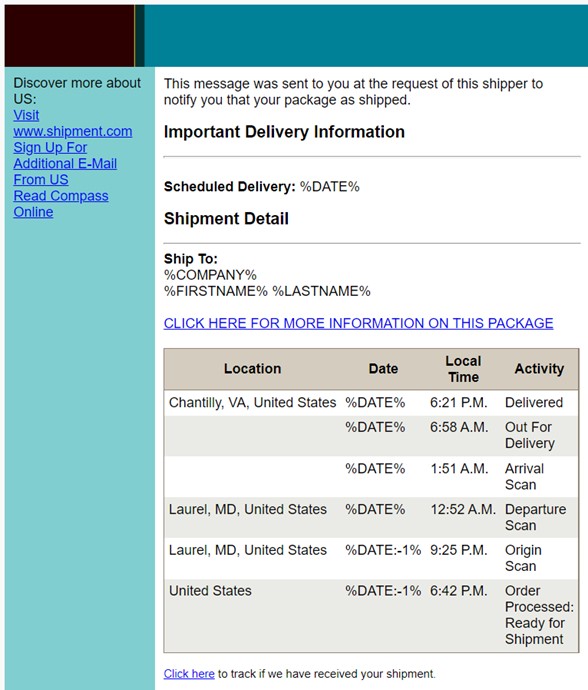 Fig. 2: Attackers leverage nearly identical shipping formats and messaging to build trust with users.
Fig. 2: Attackers leverage nearly identical shipping formats and messaging to build trust with users.
Attackers don't simply leverage engaging messaging; they also copy familiar template structures used by FedEx, UPS, and other delivery services, making it appear legitimate and trustworthy. People regularly shop online, so sensitive work information can get compromised if users fall for an attack. It's critical that users always stay vigilant and can recognize phishing emails as realistic as the one above to ensure the safety of your organization and sensitive data.
Attackers use current events to increase urgency and clicks on malicious content
As we enter year three of the COVID-19 pandemic, messages that provide "precautionary measures" in the workplace will surely capture people's attention.
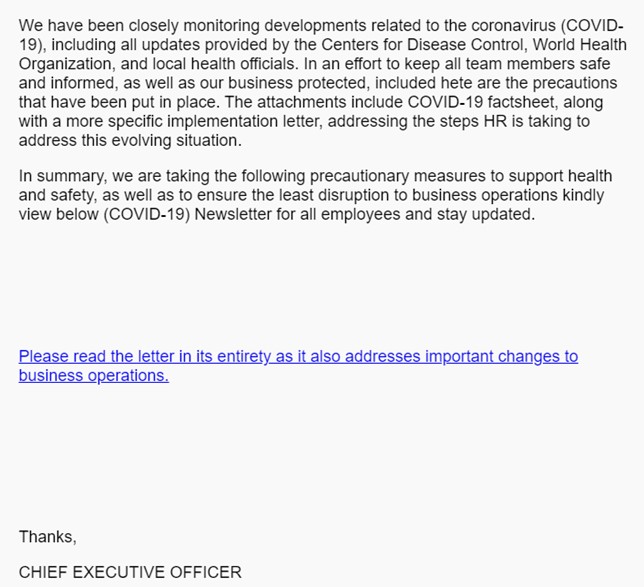 Fig. 3: COVID-19 emails with important information related to precautionary measures appear legitimate and trustworthy.
Fig. 3: COVID-19 emails with important information related to precautionary measures appear legitimate and trustworthy.
In the email above, the attacker uses professional language and seeks to trick users into clicking a link that will show them the new regulations in the workplace to keep people safe from infection. It builds user trust by appearing to come from the Chief Executive Officer at the company and adds credibility by mentioning the CDC, WHO, and even HR as being involved in providing updates.
A strong security awareness education can set the right foundational knowledge to educate users on how to spot clues that indicate a phishing email despite the clever social engineering tactics employed.
Use the Proofpoint Phishing Awareness Kit to raise phishing awareness and educate your users
Cybersecurity education and best practice tips are key to helping users stay safe. We've curated a selection of resources to help your users:
• Effectively identify phishing emails inside and outside the workplace
• Report phishing to the organization
• Understand the consequences phishing emails can have on data loss and account compromise
The Proofpoint Phishing Awareness Kit provides written, visual, and video content that can be emailed, displayed, posted, or presented throughout the next few weeks. You'll find descriptions on how to use the materials and a suggested communication plan and schedule.





