Along with all the news surrounding cryptocurrencies, non-fungible tokens (NFTs) are making headlines of their own. The somewhat complicated to understand digital images have mostly made noise due to the exorbitant amount of money people are willing to pay to "own" one. But they have now become another target of cybercriminals.
Check Point has published a report detailing a phishing campaign targeting the popular NFT trading platform OpenSea, which is currently valued at $13.3 billion and one of the largest peer-to-peer NFT marketplaces in the world.
The threat actor(s) behind the phishing campaign was able to transfer more than $2 million in Ethereum to his digital wallet, all from selling stolen NFTs.
Phishing for NFTs
Only a few days ago, OpenSea announced a planned contract migration to address the existing inactive listings of old NFTs. This requires all users to migrate their listings on Ethereum to the new smart contract.
The company emailed instructions to all its users, explaining how the process would work. But the threat actor was quick to take advantage of this planned migration, sending a copy of the same email with a malicious link. Here is what the original email looked like:
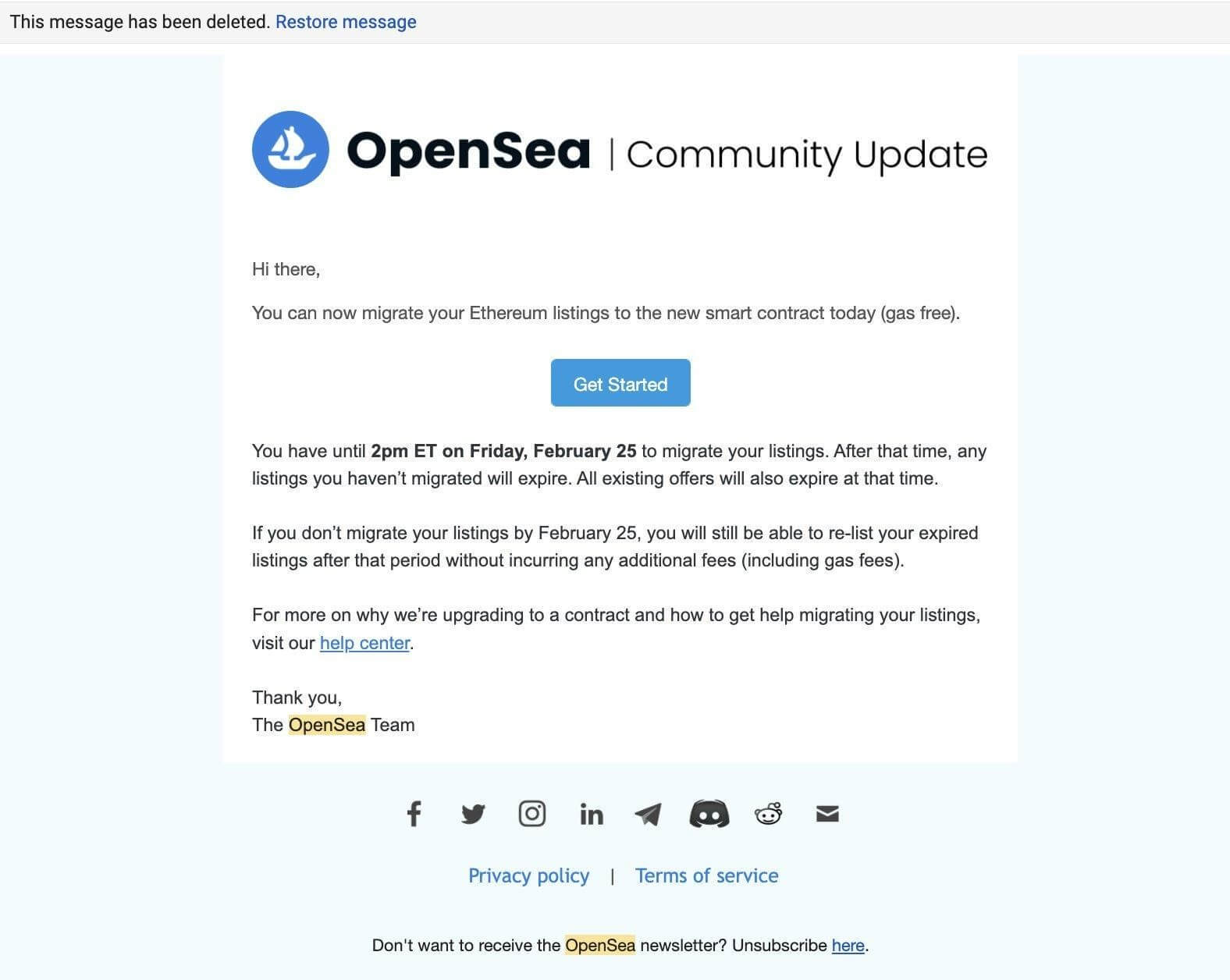
After clicking on the link, users were redirected to a fake OpenSea website where it would ask them to sign a transaction that looked legitimate. You can see the similar images shared by Check Point:
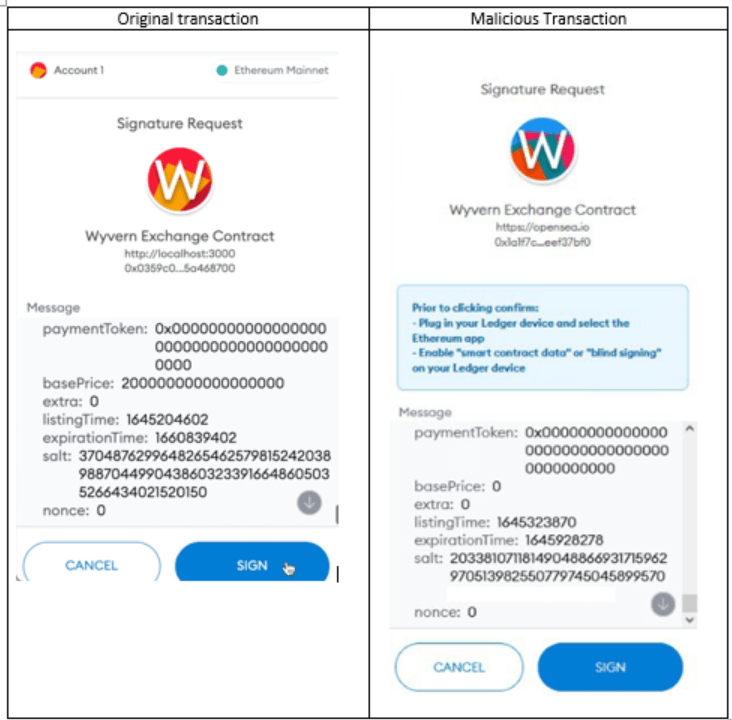
After signing the transaction, an atomicMatch_ request would be sent to the attacker contract, which he created a month ago prior to the attack.
Next, the atomicMatch_ would be forwarded to the OpenSea contract. atomicMatch_ in OpenSea is responsible for all the trading on OpenSea with minimal trust. Atomic means that the transaction will only take place if all the parameters of the transaction are met. And this is how all the NFTs are moving around accounts at OpenSea.
Which is why the attacker decided to use the atomicMatch_ to steal the victims' NFTs because this kind of request is capable of stealing all victim NFTs in one transaction, according to Check Point.
Researchers says the attack flow goes like this:
- Victim clicks on a malicious link from the phishing email
- The link opens a phishing website and asks the victim to sign a transaction.
- By signing the transaction an atomicMatch_ request would be sent to 0xa2c0946ad444dccf990394c5cbe019a858a945bd (attacker contract).
- Attacker than forward the request at atomicMath at 0x7be8076f4ea4a4ad08075c2508e481d6c946d12b (OpenSea contract)
- OpenSea Contract verifies all the parameters of the deal and executes the transaction because everything is signed by the victim and approved.
- OpenSea contract communicate with the NFT contracts and transfer the NFT from the victim to the attacker according to the atomicMatch."
The whole process looks like this:
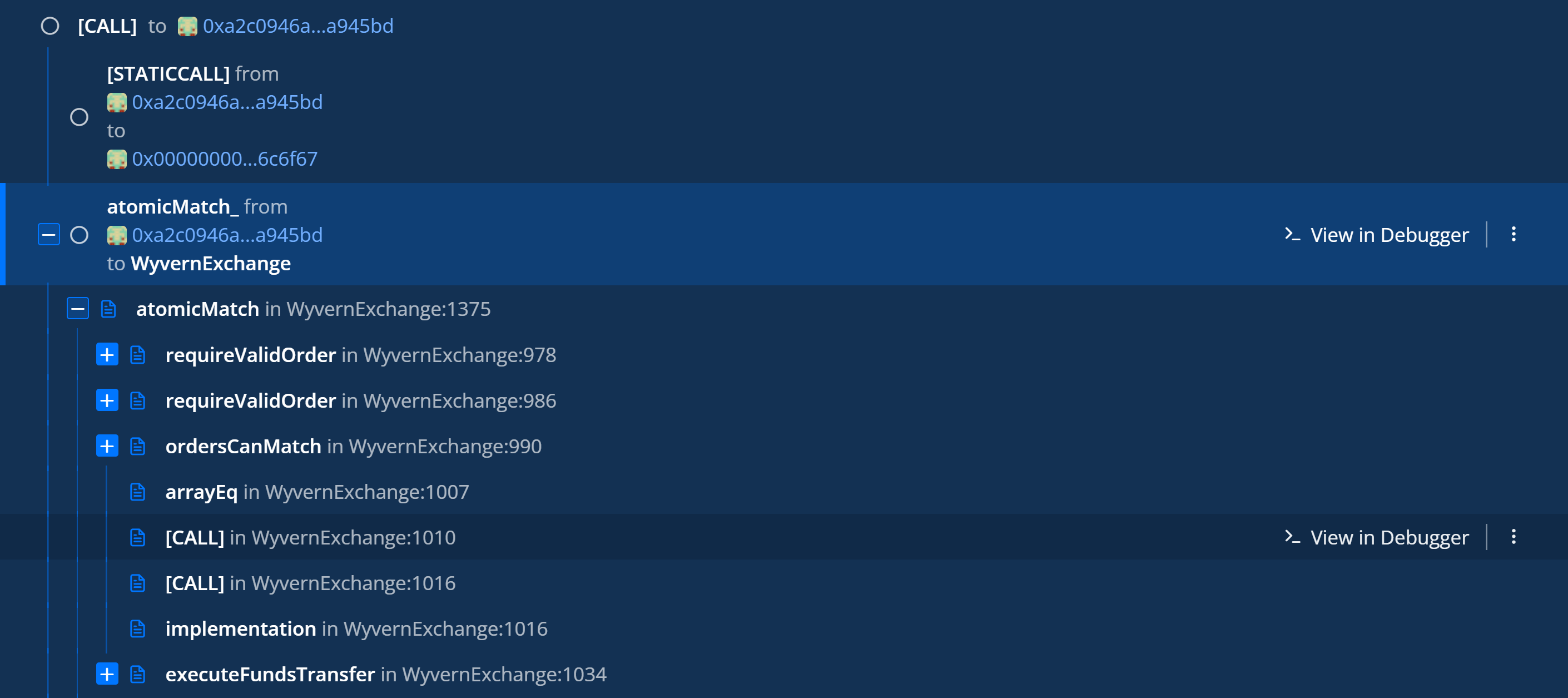
An interesting discovery security researchers made was that the threat actor executed a dry run before the attack, trying to execute an atomicMatch_ to OpenSea and verify their attack.
For more information the NFT theft, see Check Point's report on the attack.





