Patching vulnerabilities is a constant battle for organizations, which is why threat actors frequently exploit dated and publicly known vulnerabilities.
But which ones, specifically? The answers arrived this week.
The United States, the United Kingdom, and Australia issued a joint cybersecurity advisory looking at the top Common Vulnerabilities and Exposures (CVEs) exploited in 2020 and 2021.
Cybersecurity advisory on top CVEs
One of the key findings in the advisory is that four of the most targeted vulnerabilities in 2020 involved remote work, VPNs, or cloud-based technologies. This trend has continued into 2021 and for the foreseeable future as many organizations have adapted to remote work in some way.
Eric Goldstein, Executive Assistant Director for Cybersecurity at CISA, had this to say about the advisory:
"In cybersecurity, getting the basics right is often most important. Organizations that apply the best practices of cybersecurity, such as patching, can reduce their risk to cyber actors exploiting known vulnerabilities in their networks. Collaboration is a crucial part of CISA’s work and today we partnered with ACSC, NCSC and FBI to highlight cyber vulnerabilities that public and private organizations should prioritize for patching to minimize risk of being exploited by malicious actors."
The advisory provides the top 30 vulnerabilities exploited in 2020 and that continue to be exploited in 2021.
Below you can see what the agencies believe to be the top regularly exploited CVEs in 2020:
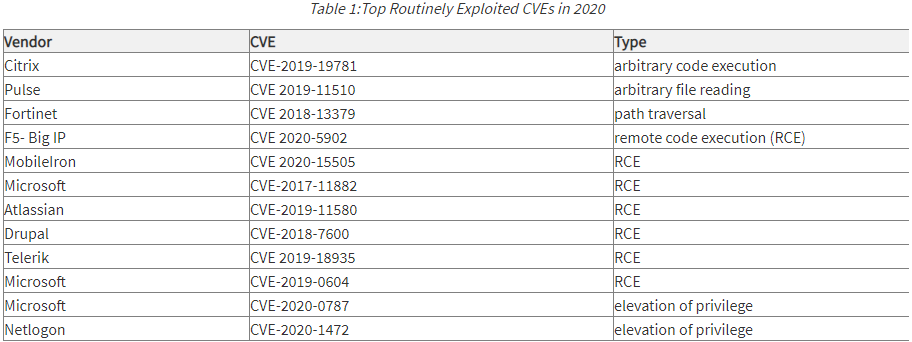
Organizations are highly encouraged to mitigate these vulnerabilities as quickly as possible to reduce risk, as most of them can be fixed by simple patching and updating of systems.
As for CVEs in 2021, the advisory says threat actors continue to target vulnerabilities in perimeter-type devices. Here is a list of CVEs in 2021 organizations need to prioritize patching for:
- Microsoft Exchange: CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065
- See CISA's Alert: Mitigate Microsoft Exchange Server Vulnerabilities for more information on identifying and mitigating malicious activity concerning these vulnerabilities.
- Pulse Secure: CVE-2021-22893, CVE-2021-22894, CVE-2021-22899, and CVE-2021-22900
- See CISA's Alert: Exploitation of Pulse Connect Secure Vulnerabilities for more information on how to investigate and mitigate this malicious activity.
- Accellion: CVE-2021-27101, CVE-2021-27102, CVE-2021-27103, CVE-2021-27104
- See the Australia-New Zealand-Singapore-UK-U.S. Joint Cybersecurity Advisory: Exploitation of Accellion File Transfer Appliance for technical details and mitigations.
- VMware: CVE-2021-21985
- See CISA's Current Activity: Unpatched VMware vCenter Software for more information and guidance.
- Fortinet: CVE-2018-13379, CVE-2020-12812, and CVE-2019-5591
- See the CISA-FBI Joint Cybersecurity Advisory: APT Actors Exploit Vulnerabilities to Gain Initial Access for Future Attacks for more details and mitigations.
For more technical information, mitigations, and indicators of compromise on the top vulnerabilities of 2020 and 2021, read the full cybersecurity advisory, Top Routinely Exploited Vulnerabilities (AA21-209A).





