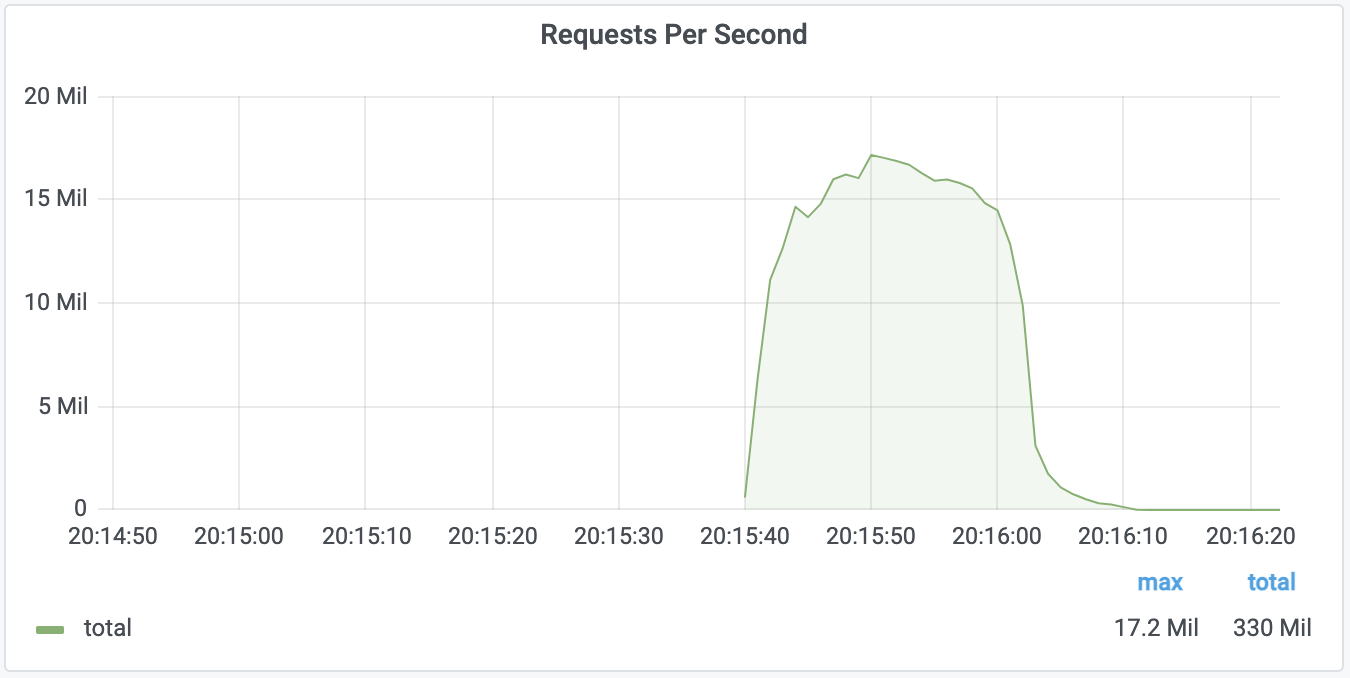
Security firm Cloudflare successfully detected and mitigated a DDoS attack that peaked at 17.2 million requests-per-second (RPS), nearly three times the size of the previous record.
The attack targeted one of Cloudflare's customers in the financial industry.
Omer Yoachimik, Product Manager of Cloudflare's DDoS Protection Service, discusses the scale of the attack:
"For perspective on how large this attack was: Cloudflare serves over 25 million HTTP requests per second on average. This refers to the average rate of legitimate traffic in 2021 Q2. So peaking at 17.2 million rps, this attack reached 68% of our Q2 average rps rate of legitimate HTTP traffic."
Although it lasted less than one minute, the powerful botnet behind the attack was able to hit the company with over 330 million attack requests.
Here is a graph of the RPS over time:
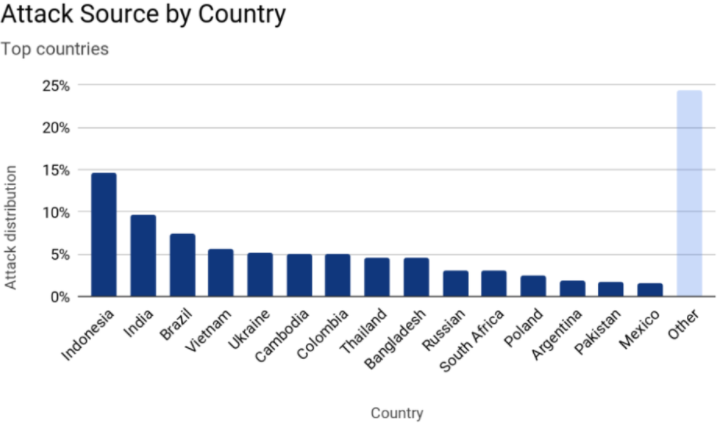
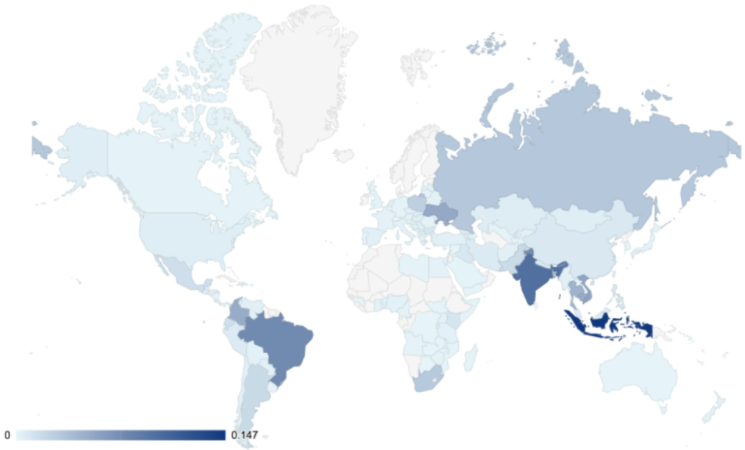
The attack had quite the range, with over 20,000 bots in 125 countries. Fifteen percent of the bot's IP addresses were located in Indonesia, while 17% came from India and Brazil combined, meaning there is a chance many devices in these countries are infected with malware.
Here is a breakdown of attack source by country:
How did Cloudflare defend against this DDoS attack?
Cloudflare was able to fend off an attack of this scale with its autonomous edge DDoS protection system. Here is how the company describes its system:
"The system is powered by our very own denial of service daemon (dosd). Dosd is a home-grown software-defined daemon. A unique dosd instance runs in every server in each one of our data centers around the world. Each dosd instance independently analyzes traffic samples out-of-path. Analyzing traffic out-of-path allows us to scan asynchronously for DDoS attacks without causing latency and impacting performance.
DDoS findings are also shared between the various dosd instances within a data center, as a form of proactive threat intelligence sharing.
Once an attack is detected, our systems generate a mitigation rule with a real-time signature that matches the attack patterns. The rule is propagated to the most optimal location in the tech stack."
Mirai malware returns
Mirai, a prominent malware strain discovered in 2016, appears to be making a comeback, according to Cloudflare.
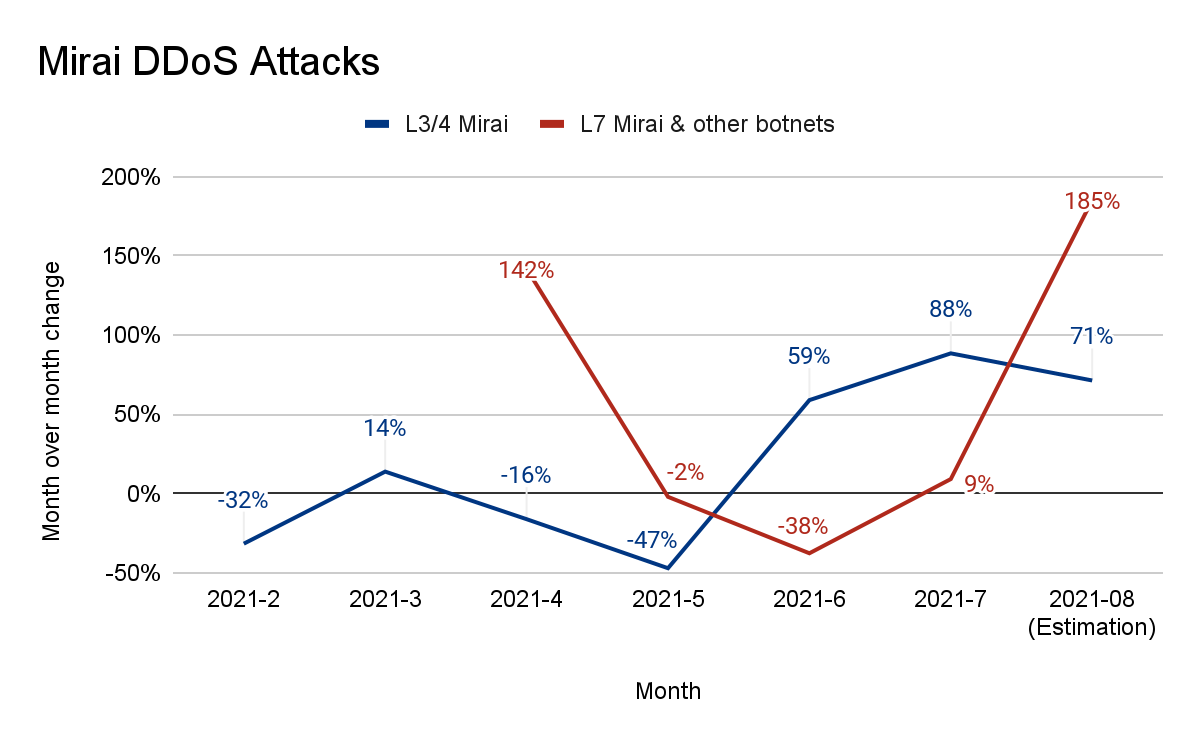
The company says it recently observed a Mirai-variant botnet that launched over a dozen DDoS attacks that peaked just below 8 million RPS. One of the targets was a major APAC-based internet services, telecommunications, and hosting provider, while another was a gaming company.
The attacks were automatically detected and mitigated without human intervention.
Cloudflare describes how Mirai attacks work:
"The malware spreads by infecting Linux-operated devices such as security cameras and routers. It then self-propagates by searching for open Telnet ports 23 and 2323. Once found, it then attempts to gain access to vulnerable devices by brute forcing known credentials such as factory default usernames and passwords. Later variants of Mirai also took advantage of zero-day exploits in routers and other devices. Once infected, the devices will monitor a Command & Control (C2) server for instructions on which target to attack."
Here is a look at how Mirai attacks have increased in the last couple months:
For more information on the record-setting DDoS attack and everything related, see Cloudflare's blog post.





