Axie Infinity, a video game that utilizes NFTs and Ethereum-based cryptocurrencies, lost $540 million in March of this year after a senior engineer was tricked into opening a PDF of a fake job application, according to a story from The Block.
The United States government has attributed the hack to a North Korean state-sponsored advanced persistent threat (APT) known as the Lazarus Group. The Cybersecurity and Infrastructure Security Agency (CISA) issued a warning in April that the group was targeting cryptocurrency and blockchain companies and that it was using social engineering schemes to gain access to the victim's network.
So, what exactly happened with Axie Infinity?
Workers at the game's developer, Sky Mavis, were approached by individuals representing a fake company whoencouraged them to apply for jobs. A source close to the situation said that the approaches came through LinkedIn.
After several interview rounds, one worker was offered a job that had an "extremely generous compensation package." The offer was emailed as a PDF document, and once it was downloaded, spyware infected the company's systems.
This might be a good time to remind everyone that if you get a job offer that is too good to be true, then it probably is.
The threat actors then proceeded to take over four out of nine validator nodes on the network. The validators fulfill various functions in blockchains, including the creation of transaction blocks and the updating of data oracles. But to move funds around, five of the nine validators must approve of the transaction, so the cybercriminals were still one short.
Sky Mavis said in its postmortem that the threat actors used the Axie DAO (decentralized autonomous organization) to get the last validator. Sky Mavis explains:
"The validator key scheme is set up to be decentralized so that it limits an attack vector, similar to this one, but the attacker found a backdoor through our gas-free RPC node, which they abused to get the signature for the Axie DAO validator.
This traces back to November 2021 when Sky Mavis requested help from the Axie DAO to distribute free transactions due to an immense user load. The Axie DAO allowlisted Sky Mavis to sign various transactions on its behalf. This was discontinued in December 2021, but the allowlist access was not revoked.
Once the attacker got access to Sky Mavis systems they were able to get the signature from the Axie DAO validator by using the gas-free RPC.
The vulnerability was fixed by adding additional validator nodes."
Sky Mavis now has 11 nodes, with a long-term goal of having 100 total.
The employee who fell for the social engineering scheme no longer works for Sky Mavis.
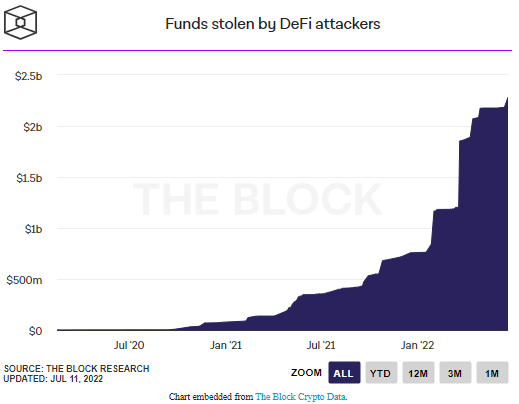
This recent incident is part of a growing trend in cybercrime, in which threat actors target all kinds of decentralized finance (DeFi) platforms. Since the pandemic, cryptocurrencies exploded in popularity, so it only makes sense that cybercrime targeting crypto would also increase.
The chart below, from The Block, shows how the amount of funds stolen has increased in the last couple years:
Follow SecureWorld News for more stories in cybersecurity.





