Within the last week, there have been some significant victories in combatting Russian cybercrime, as the country continues its brutal and unprovoked invasion of Ukraine.
U.S. and German authorities shutdown the largest darknet marketplace in the world, the Department of Justice disrupted a botnet controlled by Russia's Main Intelligence Directorate (GRU), and Microsoft announced it had successfully blocked cyberattacks from Russia targeting Ukraine.
To add to this growing list of victories, there are reports that some Russian threat actors affiliated with Anonymous have turned against their own country and are using ransomware to attack organizations based in Russia.
The hacking group named Network Battalion 65, better known as NB65, is using the infamous cyber gang Conti's leaked ransomware source code to create its own ransomware to use on Russian organizations, according to Bleeping Computer.
NB65 uses Conti ransomware to target Russia
Earlier this year, the Conti ransomware source code was leaked after the gang announced its support for Putin and the invasion of Ukraine. Along with the source code, over 170,000 internal messages were exposed.
Bleeping Computer reports that almost all antivirus vendors detect the code being used by NB65 as Conti, and Intezer Analyze also determined it uses 66% of the same code as the usual Conti ransomware samples.
You can see an example of a ransomware note from NB65 below:
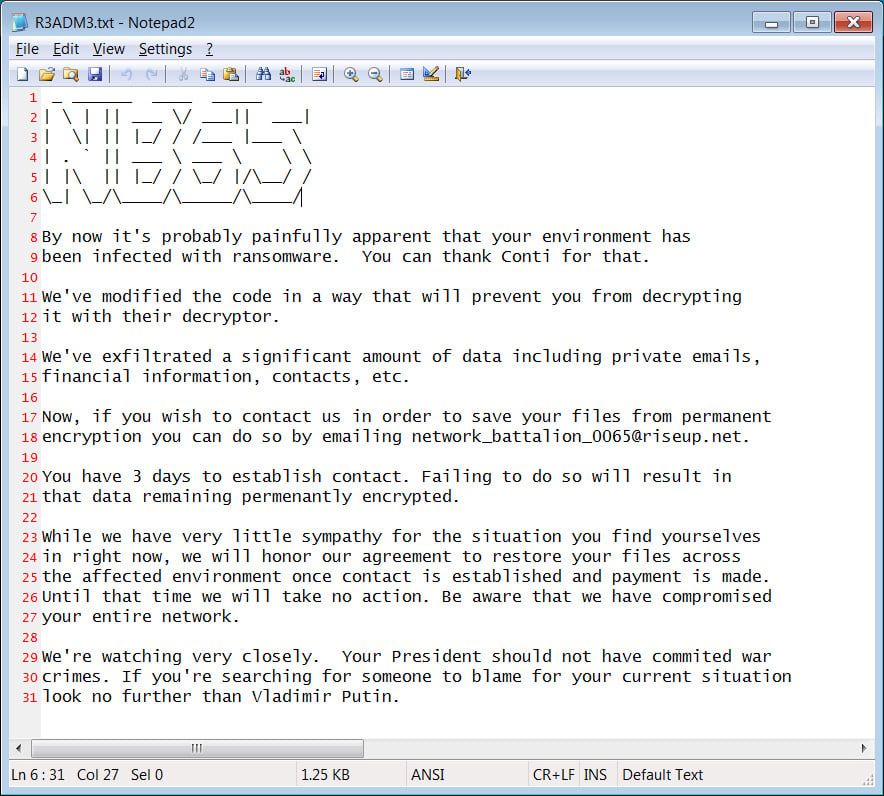
Russian organizations that claim to have been attacked by NB65 include document management operator Tensor, Russian space agency Roscosmos, and the state-owned media company VGTRK.
The VGTRK incident allegedly left 786.2 GB of data encrypted, which includes 900,000 emails and 4,000 files. NB65 tweeted this out in late March:
The All-Russian State Television and Radio Broadcasting Company (VGTRK), propaganda branch of the Russian Federation can fuck themselves. @Telecomix is going to have some fun parsing through this. #datalove @YourAnonNews @ITarmyUA Glory to Ukraine! Full dump will be ready soon. pic.twitter.com/3foAOAYBDv
— NB65 (@xxNB65) March 25, 2022
Though NB65's ransomware is largely based on Conti's, existing decryptors won't work for those infected. An NB65 representative spoke about the difference:
"It's been modified in a way that all versions of Conti's decryptor won't work. Each deployment generates a randomized key based off of a couple variables that we change for each target. There's really no way to decrypt without making contact with us."
The same spokesperson also discussed the true purpose of the group:
"After Bucha we elected to target certain companies, that may be civilian owned, but still would have an impact on Russia's ability to operate normally. The Russian popular support for Putin's war crimes is overwhelming. From the very beginning we made it clear. We're supporting Ukraine. We will honor our word. When Russia ceases all hostilities in Ukraine and ends this ridiculous war NB65 will stop attacking Russian internet facing assets and companies.
Until then, f*** em.
We will not be hitting any targets outside of Russia. Groups like Conti and Sandworm, along with other Russian APTs have been hitting the west for years with ransomware, supply chain hits (Solarwinds or defense contractors)... We figured it was time for them to deal with that themselves."
NB65 also tweeted that it would not be attacking any organizations outside of Russia, and that all ransomware payments received would be donated to help Ukraine during this incredibly difficult time.
See the original story from BleepingComputer for more information.





